A new ransomware called Vovalex is being distributed through fake pirated software that impersonates popular Windows utilities, such as CCleaner.
When it comes down to it, all ransomware infections boil down to the same function – encrypt a device’s files and then drop a ransom note demanding payment in some form.
While Vovalex is no different, what stands out to Advanced Intel’s Vitali Kremez is that it may be the first ransomware written in D.
2021-01-29: #Vovalex #Ransomware … in #Dlang or ‘D’|x64 ~32mb Size
Probably First Documented Ransomware Written in ‘D’
Dlang Section Headers with “dmd” Compiler
1._deh
2.dp
3.minfo
4.tpXMR Monero Extortion |D Likely Used to Bypass AV Detection
h/t @malwrhunterteam pic.twitter.com/XBjpsrbMLS— Vitali Kremez (@VK_Intel) January 29, 2021
According to the D website, Dlang is inspired by C++ but shares components from other languages.
“D is the culmination of decades of experience implementing compilers for many diverse languages, and attempting to construct large projects using those languages. D draws inspiration from those other languages (most especially C++) and tempers it with experience and real world practicality,” states the D website.
As malware developers do not commonly use Dlang, Kremez believes that the attackers are using security software to bypass detections.
Vovalex is distributed as pirated software
Vovalex was first discovered by MalwareHunterTeam, who shared a sample [VirusTotal] with BleepingComputer so we can take a look.
The shared sample analyzed by BleepingComputer is distributed as a warez copy of the CCleaner Windows utility, as can be seen by the bundled NFO file below.
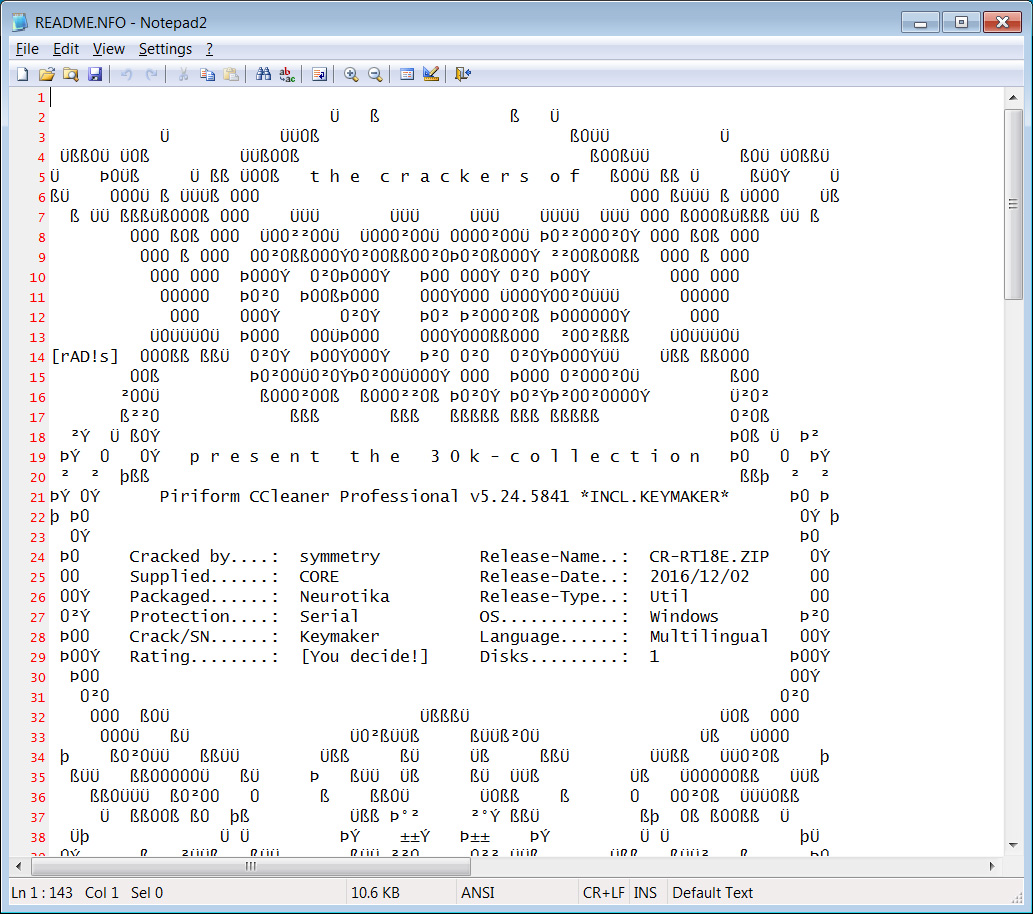
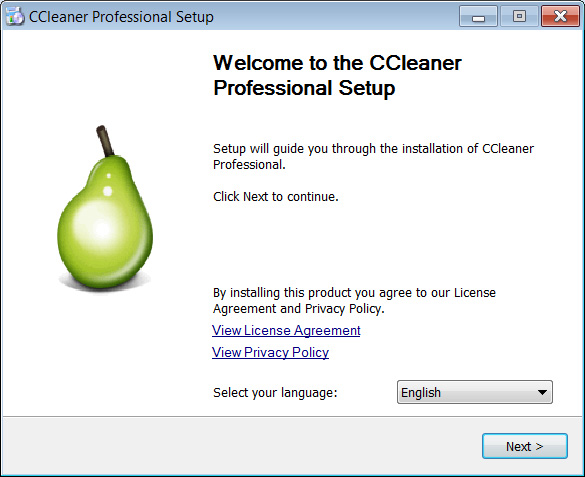
When executed, the ransomware will launch a legitimate CCleaner installer and copy itself to the random file name in the %Temp%folder.
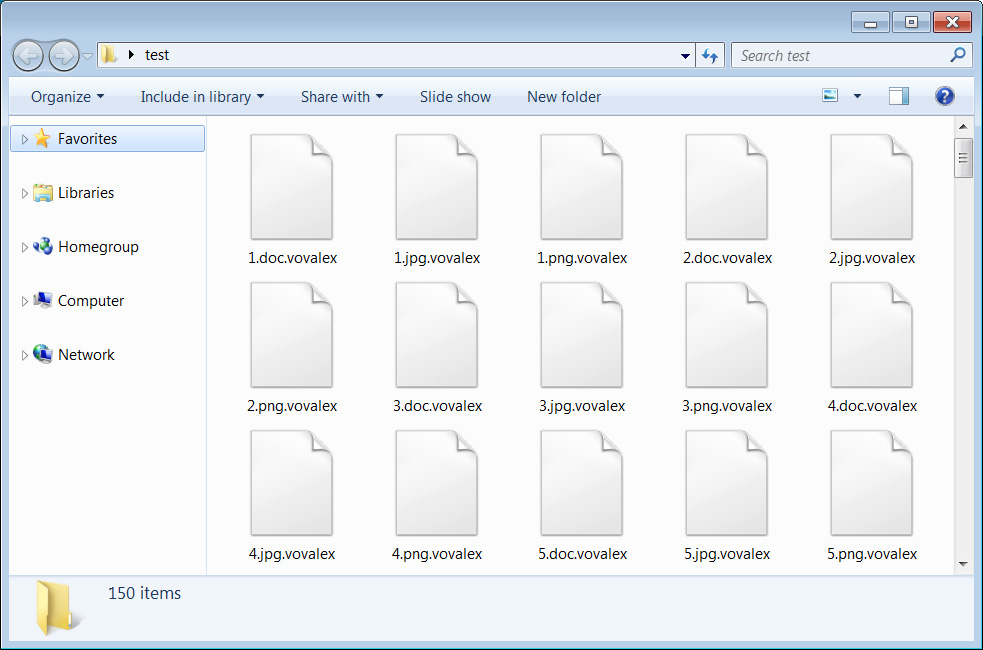
The ransomware will begin to encrypt files on the drive and append the .vovalex extension to encrypted file’s names.
When done, the ransomware will create a ransom note named README.VOVALEX.txt on the desktop that asks for 0.5 XMR (Monero) to retrieve a decryptor. This amount is equal to approximately $69.54 at current prices.

At this time, it is unknown if researchers can decrypt the ransomware for free.
Thankfully, Vovalex is not widely distributed at this time. If the threat actors partner with fake crack sites and adware bundles, similar to how STOP ransomware is distributed, then we may have a bigger problem on our hands.
