Blockchain & Cryptocurrency
,
Cryptocurrency Fraud
,
Cybercrime
Ransomware Victims Typically Charged Less for Paying With Tougher-to-Trace Monero
While almost all ransomware-wielding attackers accept Bitcoin for ransom payments, many continue to prefer Monero, thanks to the privacy-preserving coin being tougher for law enforcement officials to track.
See Also: Live Webinar Today | NSM-8 Deadline July 2022:Keys for Quantum-Resistant Algorithms Implementation
As police increasingly crack down on Bitcoin-using criminals, however, experts say this could push more ransomware operations to demand Monero, or to rapidly convert received funds into that virtual currency.
“Bitcoin remains the dominant player in ransom demands with Monero emerging as the main alternative,” says Jason Rebholz, CISO at Boston-based commercial insurance provider Corvus Insurance.
That situation remains largely extant since at least early 2020, when the notorious and perhaps now defunct REvil – aka Sodinokibi – operation began demanding ransoms be paid in Monero cryptocurrency, aka “crypto.” But victims could request to pay in Bitcoin, aka BTC, and these requests tended to be granted, albeit with a 10% premium applied, says cryptocurrency intelligence group CipherTrace, which since last September has been part of Mastercard.
The Alphv/BlackCat ransomware operation that appeared late last year also prefers to receive ransom payments in Monero. The group, which is a rebranding of the DarkSide group that hit Colonial Pipeline in May 2021 with disastrous effect, and which was then doing business as BlackMatter, has continued to charge a 15% premium if victims opt to pay with Bitcoin instead of Monero.
Monero: Privacy-Preserving Coin
The open-source community project team that runs Monero bills transactions conducted using the digital currency as being “confidential and untraceable,” thanks to it using “various privacy-enhancing technologies to ensure the anonymity of its users.”
“Monero is considered to offer better anonymity, with various protections offered that can shield transactions from scrutiny,” CipherTrace says. “The ability to track these payments varies, but Monero is more challenging than the completely public Bitcoin blockchain.”
But criminals’ main impetus remains getting paid. “A number of groups make demands in both currencies, but will generally accept either,” says Bill Siegel, CEO of ransomware incident response firm Coveware, based in Westport, Connecticut. “The privacy coins make the laundering process easier for them, so they obviously prefer it, but they will still accept BTC.”
Supply, however, can be a challenge with Monero and lesser-used cryptocurrency. “Most ransom payments are still made in Bitcoin as there is far more liquidity and it is much easier to source,” says Ari Redbord, head of legal and government affairs at blockchain analytics firm TRM Labs and a contributor to Information Security Media Group. “Many compliant exchanges have de-risked Monero and other privacy coins based on industry and government pressure.”
Why Bitcoin Payments Carry a Premium
Not just Alphv/BlackCat, but most ransomware groups that accept Monero typically add a 5% to 20% premium for victims that want to pay in Bitcoin, says attorney Guillermo Christensen, a partner at Indianapolis-based law firm Ice Miller. Christensen manages its Washington office and specializes in cybersecurity planning and incidents, including around ransomware.
Even so, only about 5% to 10% of the ransomware incidents he’s worked on have ever involved a payment in Monero. “It is definitely more than it was, but it’s not a huge element in this,” he says.
Bitcoin remains “the prominent crypto requested by threat actors,” although most will accept multiple types of virtual currency,” says attorney Catherine Lyle, who’s head of claims at Coalition, a San Francisco-based cybersecurity insurance company.
“Instead of it being a matter of ‘only accepting Bitcoin,’ we have received demands in Monero with an upcharge of 10% to 15% if payment is made via Bitcoin,” Lyle says. “The reasoning is simple: Monero, also known as XMR, is a privacy-focused crypto. Monero is less traceable and gives more anonymity.”
Experts say criminals will sometimes accept other types of cryptocurrency too, such as Dash – known for its anonymity – but add that overall, such payments account for an extremely small fraction of all ransoms paid.
Laundering Bitcoin Costs Extra
Little about the underlying calculus seems to have changed for criminals in recent years: Ransomware operations seek anonymity, and obscuring Bitcoin transactions costs more, says Coveware’s Siegel.
“The hype and concern about privacy coins has never really changed,” he says. “Cybercriminals have always used techniques like chain hopping to launder their proceeds and try to obfuscate the money trail. This is not new.”
Chain hopping involves jumping between different cryptocurrencies to try and obscure the money trail. Another service offered on the cybercrime underground is a peel chain, in which a small amount of funds gets continually peeled off and routed through other addresses.
Another common money laundering service: bitcoin mixers or tumblers, which attempt to obscure the connection between the address from which bitcoins originated and to which they get sent. Mixing providers typically charge a percentage of any funds they’ve helped obscure.
Chatter on cybercrime forums suggests that mixing Monero isn’t necessary, given in-built features designed to obscure the flow of transactions. Nevertheless, when the AlphaBay darknet market relaunched last year, one of the services it advertised was a Monero mixer.
No cryptocurrency, however, offers complete anonymity. When law enforcement officials bust suspected criminals and conduct a digital forensic investigation of their systems, for example, investigators may identify cryptocurrency wallets tied to illicit activities. Likewise, the FBI and other law enforcement agencies continue to appeal to victims for intelligence tied to attacks, including the addresses of any wallets to which they may have paid a ransom (see: FBI Alert: Have You Been Bitten by BlackCat Ransomware?).
Such intelligence helps them better trace the flow of illicit funds and identify additional suspects, no matter the steps they may have taken to try and obscure those activities.
Follow the Money
Intelligence analysts can assess what types of cryptocurrency ransomware groups accept by identifying wallets tied to the group that appear to receive ransom payments (see: Ransomware Proceeds: $400 Million Routed to Russia in 2021).

In February, New York-based blockchain intelligence firm Chainalysis reported that it had so far identified $602 million known to have been received by ransomware addresses in 2021, and $692 million in 2020. Those figures will likely keep increasing as law enforcement agencies and private firms amass fresh intelligence tying individual criminals or syndicates to specific wallet addresses.
While an increasing number of ransomware groups have ties to Monero wallets, intelligence firms report that Bitcoin overwhelmingly dominates. “While we have a list of over 50 groups and strains that use XMR, the list of those using BTC is well over 1,000,” CipherTrace says. “As ransomware strains come and go, most of those will no longer be active but BTC is still the dominant cryptocurrency used among criminals.”
The Financial Crimes Enforcement Network, which is a bureau of the U.S. Department of the Treasury, last October reported that transactions in Monero comprised only a small portion of the suspicious activity reports, or SARs, that it received from financial services firms.
All firms that handle cryptocurrency globally are required to comply with U.S. anti-money laundering and “know your customer” rules. This includes filing SARs whenever designated types of activities occur.
In October 2021, FinCEN released a ransomware report analyzing SARs received during the first half of last year. FinCEN said that the quantity of reports it received was surging, and that the total volume of ransomware-related SARs had increased from $416 million in 2020 to $590 for just the first half of 2021, averaging $66.4 million per month.
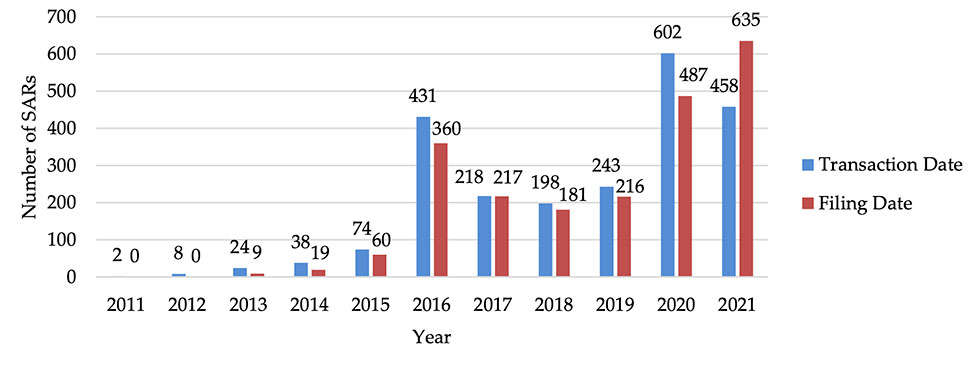
FinCEN at the time reported that the SARs tied to 68 ransomware different variants, with the most common being REvil/Sodinokibi, Conti, DarkSide, Avaddon and Phobos. Attackers demanded Bitcoin in almost every case, except about 6% of transactions, where they accepted either Bitcoin or Monero, with only Monero being accepted just 0.4% of the time, it says.
Expect Greater Use of Privacy Coins?
But as law enforcement agencies get better at tracking the flow of bitcoins, as well as ensuring that financial services firms comply with “know your customer” and anti-money laundering rules, Coalition’s Lyle says criminals’ use of Monero seems likely to increase.
“While many think of Bitcoin as allowing pure anonymity, threat actors know that transactions with Bitcoin are recorded on a blockchain that is publicly searchable,” Lyle says. “Monero does not permit use of certain tracing elements for transactions, including the wallet address of both the sender and receiver, and hinders governmental monitoring/tracking.”
Beyond ransomware groups, the administrators of some cybercrime markets have also preferred Monero. White House Market, which operated from February 2019 to October 2021, in late 2020 began only accepting Monero. When AlphaBay was relaunched in August 2021, it was as a Monero-only market.
Again, however, this doesn’t mean that Monero transactions – or users – are immune to being tracked. “Due to governmental involvement, tracing of Monero will occur due to governmental controls such as legislation, regulation and executive orders,” Lyle says. “As we have all seen, ransomware and the resultant extortion are under scrutiny by governments.”
These efforts are aimed at disrupting and unmasking criminal users of any type of cryptocurrency. “This has been seen through sanctions against nefarious crypto exchanges and increased scrutiny around AML/KYC for crypto payments,” says Rebholz of Corvus Insurance. “While ransomware actors will always enjoy a level of anonymity by leveraging cryptocurrencies, pressure will continue to mount on tracking and blocking access to illicit funds. This will likely expedite ransomware actors’ shift to anonymity-based cryptocurrencies.”
