What Is Monero?
Monero, a fork of Bytecoin, is a secure, private, and untraceable currency, built on the Cryptonote protocol using Ring Signatures. Proof of Work mechanism called CryptoNight issues new coins which incentivize miners to secure the network and validate transactions. Originally launched in April 2014 as BitMonero, Monero (symbol XMR), means money in Esperanto.
The public and hidden Monero ledger allows anyone to send and receive transactions privately. This means no outside observer would know the sender, amount, or destination.
Monero and it’s community stand by three key values: (1) Security, (2) Privacy and (3) Decentralization
The Monero website elaborates further:
Security
Users must be able to trust Monero with their transactions, without risk of error or attack.
Privacy
Monero takes privacy seriously. Monero needs to be able to protect users in a court of law and, in extreme cases, from the death penalty.
Decentralization
Monero is committed to providing the maximum amount of decentralization.
In this Monero guide, we cover everything you need to know, including:
How Does Monero Work?
Monero is based on an application level cryptographic protocol focused on privacy called Ring Signatures.
Ring Signatures were originally proposed at a 2001 Cryptography conference in Queensland, Australia. The authors of Ring Signatures include Ron Rivest, Adi Shamir, and Yael Tauman. Ring Signatures are the core mechanism behind how Monero transactions are structured after being broadcasted from the wallet.
The core use case behind Monero is how transactions are not linkable or traceable because of stealth addresses. This protects sender and receivers while also allowing selective observation of transactions through a public/private view key construct in addition to normal private/public keys (more on this later).
Monero has a variable block limit which allows flexibility in data management (block sizes) and scalability. It needs this in great part due to its architecture. Privacy requires more cryptography and data around transactions.
Ultimately, Monero uses ring signatures, ring confidential transactions (RCT), and stealth addresses to obfuscate transactions at the protocol level to protect both senders and receivers from eavesdropping while still allowing transactions to be validated by a third party if desired.
Technical Details
Launched: April 14, 2014
Total coin supply: Initially 18.4 million coins (After this, there will be a permanently fixed production of 0.3 XMR per minute to balance out lost coins per year)
Algorithm: Proof of Work (PoW) using CryptoNight
Block reward: Smoothly varying
Block time: 120 seconds
Difficulty: Retargets at every block
The Problem With Bitcoin
Fungibility allows you to exchange the same type of a good or asset with another. This implies equal value between the goods and assets. For example, you could trade one silver eagle coin for another one silver eagle coin (indicating the same value between the two coins).
But, what if you couldn’t trade your silver coin for another because that silver coin was used in illegal activity?
This is the exact conundrum that Bitcoin faces due to its completely transparent architecture. If some agency decided a certain Bitcoin transaction was used for illegal purposes, it would threaten the ability for that Bitcoin to be acceptable as a fungible currency.
This is a mission-critical construct to something being considered “money” and is disconcerting to see Bitcoin underfire. Luckily, Monero aims to fix this problem through baked in and coded privacy.
Dogbert knows what’s up. | Dilbert © 2006 Scott Adams
One of Bitcoin’s big downfalls is the lack of flexibility for the implementation of new features, which require almost complete network updating. (As we have seen with the blocksize debate)
This includes hard-coded constraints and natural elements of the design (such as block frequency, the maximum amount of money supply, and the number of confirmations required).
The traceability of transaction amounts, as well as the sender/receiver, is publicly viewable automatically with Bitcoin unless specific steps are taken by the user.
The proof of work algorithm (PoW) has also violated the original Satoshi vision of “one-CPU-one-vote” with the advent of GPU and Application Specific Integrated Circuit (ASIC) hardware. This allows those miners to gain majority control (51%+) over the network and govern changes. (Like a fork, to keep the network going.)
Irregular emission refers to the construct where the Bitcoin rewards are halved every 4 years. The original intent was to create limited smooth emission with exponent decay. (More predictable not choppy pattern)
Instead, we have a piecewise linear emission (as pictured below) which creates the opportunity for a double spend attack. This is due to the network hash rate decrease at each halving. Note the “stairwell” like moves.
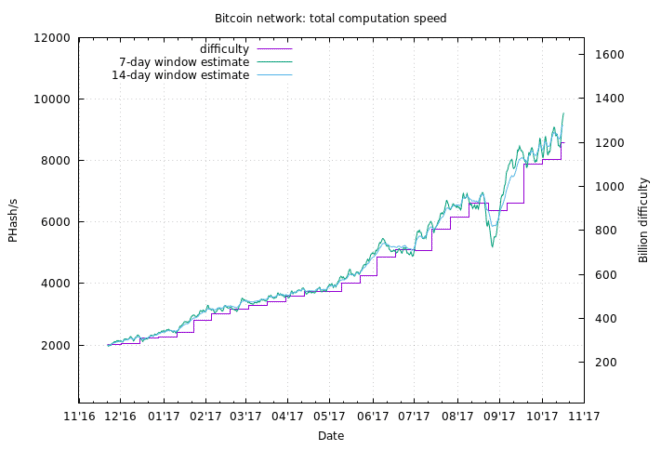
Bitcoin’s difficulty adjustments aren’t smooth.
Bytecoin Fork
Bytecoin is the first known implementation of the CryptoNote protocol with code produced entirely from scratch. But, why was Monero needed if there was already an implementation of this? Well, as always with crypto, prepare for some drama.
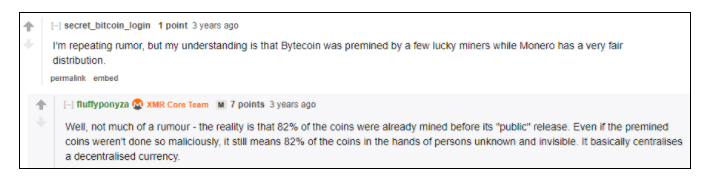
Bytecoin may have been premined.
As elaborated in this Monero subreddit from three years ago, there was not only a Bytecoin premine but also a falsifying of the blockchain to show a fair distribution. Then, there were two years of “crippled” code that could have been improved but was not. Ricardo Spagni aka “Fluffypony” said the Monero team fixed these problems in a few weeks.
Monero Team
Per the team section on the Monero website, the core team includes:
In addition, there have been over 30 developers and 420 contributors over the life of the project. As Monero is focused on privacy, it’s no surprise that many team members choose to stay anonymous
Monero Technology
The main tech behind Monero is a balance of allowing you to control your keys and operate privately with proven security mechanisms while also allowing malleability and development in the network. (E.g. variable block size, integration of Kovri)
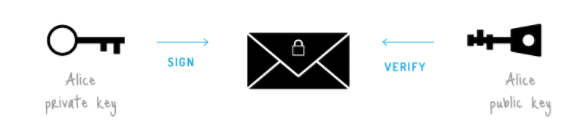
How a normal (not fully anonymous) transaction works
The default set-up for Bitcoin transactions is completely transparent and pseudonymous if steps are not taken to obscure one’s identity and transactions (e.g. a VPN and mixing services). This means your IP address can be connected to your device (i.e. personal identity) with enough resources dedicated to connecting the two.
Ring Signatures Hide Transactions
Ring Signatures are digital signatures where several signers sign a transaction. Think: signing with a joint account but with no one knowing the true signer
The sender generates a one-time spend key and the recipient is the only party that can detect and spend the money based on that key.
Key images, cryptographic keys, are derived from each output being spent and prevent double spending. This is because there’s one key image per output (expenditure) on the Blockchain.
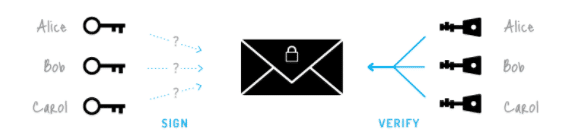
Ring Signature Transactions include multiple signers, unknown to outside observers.
A ring signature uses your account keys and selected public keys from the blockchain to form a “ring” of possible signers. The main security property of a ring signature is that it makes it impossible to see which group members’ keys produced the signature.
No outside observer can match signers in the ring ensuring that transaction outputs are untraceable. In addition, fungibility remains as the network does not know spent amounts (despite being able to validate a real transaction took place).
I’m excited to see progress on Confidential Transactions. Fungibility is the only feature of good money that Bitcoin/Litecoin is missing.
I look forward to adding this to Litecoin when it is ready. ? And this can be done with a soft fork. Stay tuned!
— Charlie Lee [LTC
] (@SatoshiLite) November 14, 2017
Ring Confidential Transactions (RCT) Hide the Amount Sent
The sender can reveal just enough information for the miners to confirm the transaction without disclosing publicly the total amount spent. (Known as a “commit”) This allows the transaction to prove its authenticity without losing privacy as a user.
The network encrypts the amount of each output and includes it in the transaction. The amount encrypted by the sender uses a shared secret built into the transaction computed by combining the recipient’s private view key with the transaction public view key (which is built in the transaction)
Third parties will not be able to view the amount based on this construct of Ring Confidential Transactions (RCT)
RingCT outputs are now mandatory as of September 2017
Stealth Addresses Protect Senders and Receivers
Moneropedia sheds light on this construct which protects senders and recipients from outside observers:
Stealth addresses are an important part of Monero’s inherent privacy. They allow and require the sender to create random one-time addresses for every transaction on behalf of the recipient.
By using stealth addresses, only the sender and receiver can determine where a payment was sent.
When you create a Monero account you’ll have a private view key, a private spend key, and a Public Address. You use he spend key to send payments, the view key to display incoming transactions, and the Public Address to receive payments. Both the spend key and view key contribute to building your Monero address. You can have a “watch only” wallet that only uses the view key.
A stealth address ultimately prevents recipient’s funds being linked with their wallet. However, a 3rd party can audit that address to prove the transaction occurred. (By the sender sharing their public view key)
The recipient gets their funds through their wallets private view key which scans the blockchain. Once detected and retrieved by the wallet, a single-use private key is created corresponding with senders public key.
The recipient can now spend those funds using their private spend key. This occurs without the sender or recipient wallets, nor the amount transacted publicly linked.
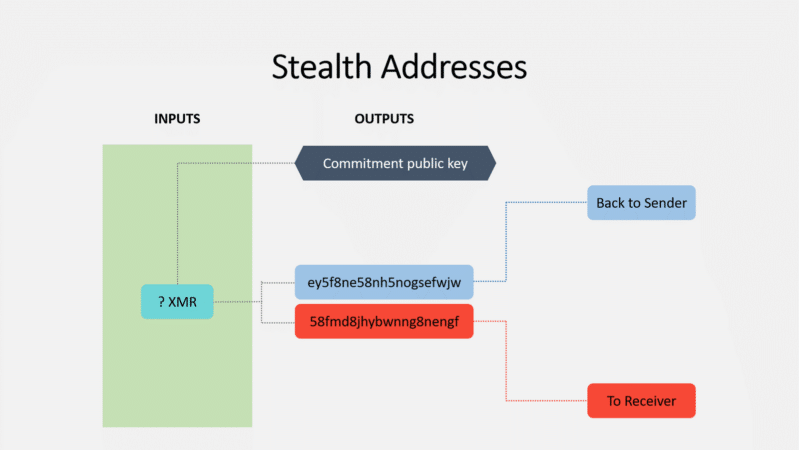
How Stealth Addresses protect Senders and Receivers | Source: Justin Ehrenhofer, Slideshare
How Monero Transactions Work
This process is very succinctly explained in this Monero Bitcointalk thread (numbers go with a picture below):
“Bob decides to spend an output, which was sent to the one-time public key. He needs Extra (1), TxOutNumber (2), and his Account private key (3) to recover his one-time private key (4). When sending a transaction to Carol, Bob generates its Extra value by random (5). He uses Extra (6), TxOutNumber (7) and Carol’s Account public key (8) to get her Output public key (9).
In the input, Bob hides the link to his output among the foreign keys (10). To prevent double-spending he also packs the Key image, derived from his One-time private key (11). Finally, Bob signs the transaction, using his One-time private key (12), all the public keys (13) and Key Image (14). He appends the resulting Ring Signature to the end of the transaction (15).”
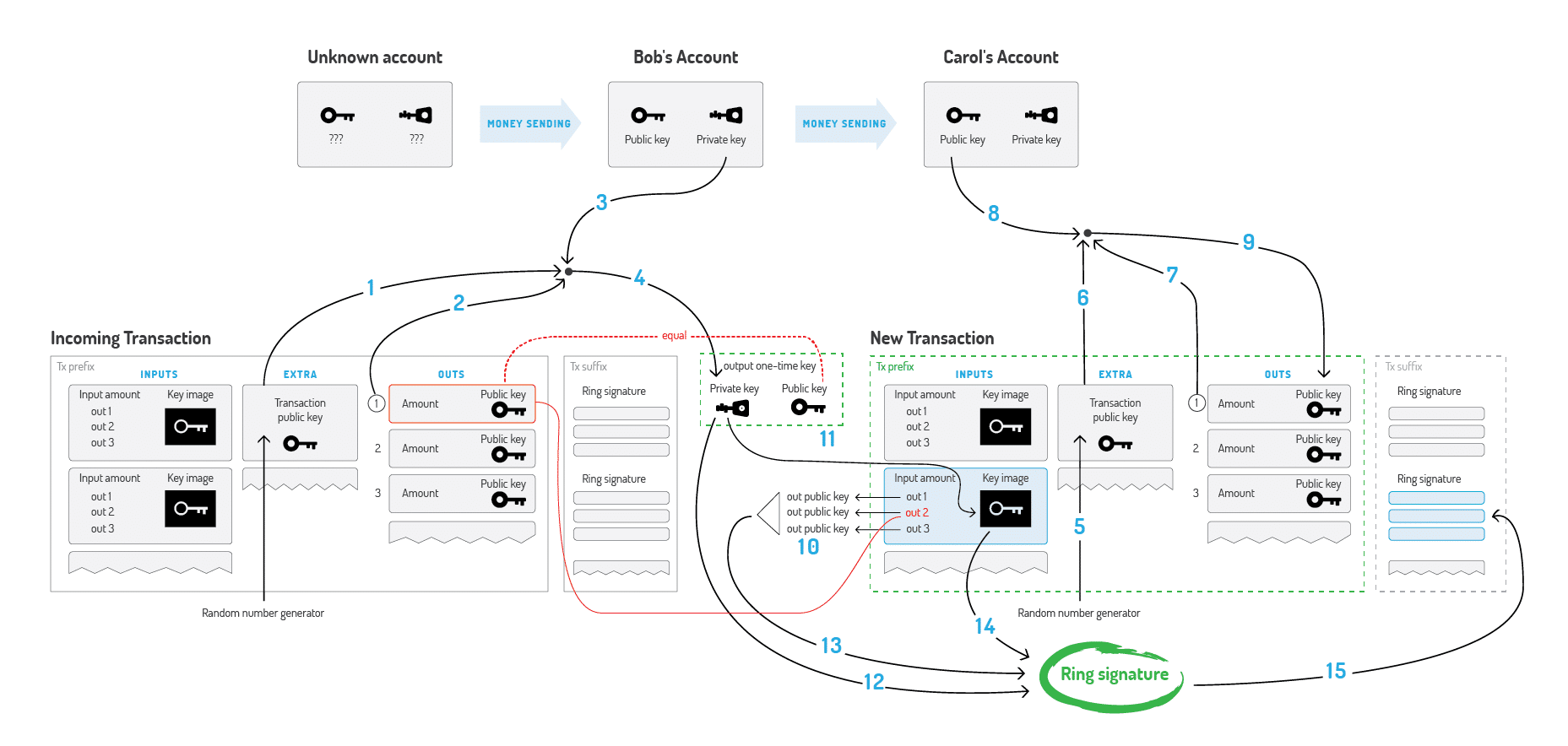
Example Monero Transaction
Competition
How does Monero compare with alternate privacy-focused solutions?
The main point of differentiation with Monero is the CryptoNote implementation, which has been around since 2001 and has received significant peer-review around its functionality. (Traceable Ring signatures for example)
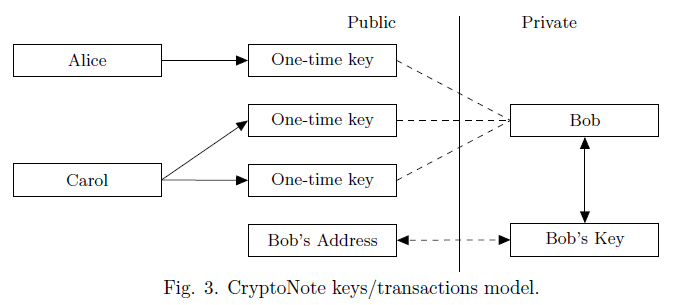
How CryptoNote Works
Two other implementations of privacy technology from other Cryptocurrencies include:
ZeroCoin/ZeroCash – Using zero-knowledge proofs (ZKPs), this protocol obscures the sender and the entire economy. You wouldn’t know any exploits (such as creating false proofs/spending) until much later due to the anonymous nature of the network. One of the biggest risks is the lack of maturity and peer review behind the cryptography. Also, ZKPs rely on the creators of the initial RSA private key to destroy it. (As supposedly done in this computer burning ceremony)
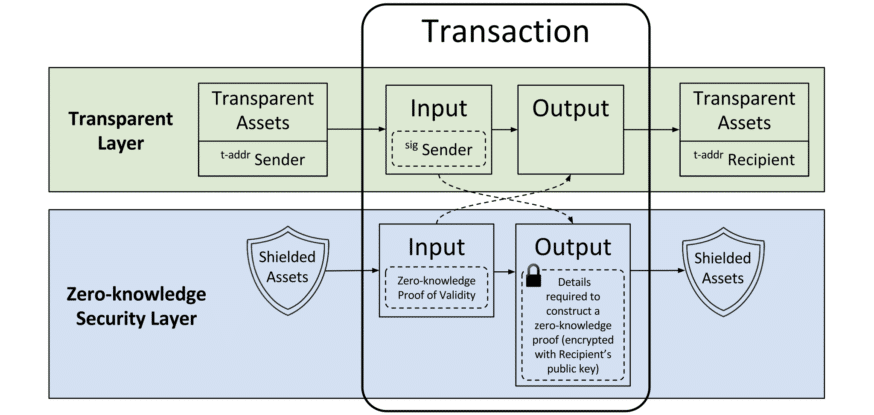
Monero vs Zcash: ZCash transactions are based on a Zero-knowledge Security Layer (ZSK)
CoinJoin is a mixing protocol that combines transactions but does not mask users, senders, or transactions at a protocol level. Originally developed by bitcoin developer Gregory Maxwell, Coin Join is used by Dash, who leverages the Masternode (MN) model where users must possess 1000 DASH to host an MN. Critics say this creates a single point of failure as the individual nodes who provide the mixing service are vulnerable to Sybil attacks.
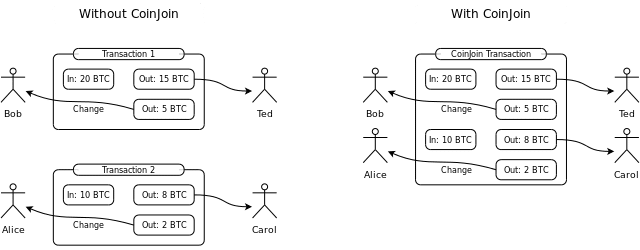
Monero vs Dash: Dash uses CoinJoin which mixes up transactions but does not provide protocol level protection of the sender and receivers.
Edward Snowden recently asked Charlie Lee, the creator of Litecoin, about Zcash vs Monero:
All private transactions
More tested privacy tech
No tax on miners to pay investors
No high inflation… better investment.@fluffypony— Charlie Lee [LTC
] (@SatoshiLite) September 29, 2017
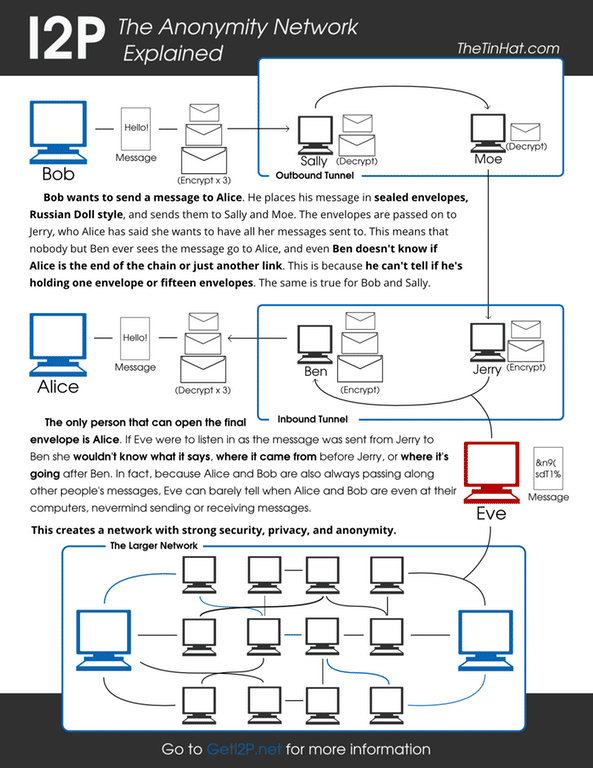
Kovri (Based on I2P) Protects Users at a Protocol Level
Kovri is a free, decentralized, anonymous network layer developed by Monero that’s based on I2P’s core specifications. I2P’s core architecture operates similarly to TOR (which uses onion) except with Kovri it uses garlic encryption and routing to create private, protected network access.
Kovri (with its garlic routing) takes things a step further than TOR by creating an anonymous, message-based overlay network of internet peers. This overlay-network helps users to hide their geographical location and internet IP address thus making internet traffic anonymous.
How Monero Split Into Five Forks (Actually Six Now)
A recent discovery of secret ASIC manufacturing of Monero miners has prompted the coin to be broken into 6 different coins.
As a result of discovering Monero ASIC manufacturing and secret mining (without the community’s knowledge), Monero decided to fork from its original algorithm due to the threat of centralized mining.
This prompted a bit of a “war against ASICs” by a community eager to preserve their core values of decentralization.
Covered more in-depth in this article, Monero has split into six different coins. These new coins include: Monero 0 (XMZ), Monero Original (XMO), Monero Classic (XMC), Monero-Classic (yep, with a dash now), MoneroC (CXMR), and just announced recently MoneroV (XMV). The original Monero (XMR) still remains as well.
Critiques, Weaknesses, and Concerns
Although it appears Monero has many accolades, what are some of its weaknesses? As discussed in this subreddit there are a few:
- Privacy – There’s been the ability to track the IP address of the node that originated a transaction. This logging of IP addresses could cause the de-anonymization of users. That being said, the Monero development is constantly improving privacy functionality and has added certain Tor capabilities to mitigate this risk.
- Mining Centralization – The majority of Monero mining used to be dominated by four pools who each had no more than 20%. This centralization is no longer that case, but it is still a potential threat.
- Darkweb PR – Although this is not a direct cause of the Monero team, it’s worth noting as the branding and public perception is always something to keep in mind and could slow adoption as people fear its use for illicit purposes.
- Transaction Size – Monero transactions are much larger than Bitcoin’s, requiring more data and causing a larger blockchain that grows daily. Fortunately, Monero forked and implemented bulletproofs in October 2018. With the implementation of bulletproofs, transaction sizes fell by up to 97 percent in some cases.
- Development Difficulty – The ability to incorporate with multi-coin wallets and other integrations that would make use more widespread have been slow.
- Limited Merchant Tools – The tools for merchants to integrate payments is difficult and hard to integrate at this time. However, there are more and more third-party services popping up to help remedy this.
Accomplishments
- Monero Transactions reduced by 97 percent – A recent hard fork upgrade implemented “bulletproofs”, a cryptographic scheme that reduces the size and cost of transactions. As a result, Monero’s transaction fees shrank by 97 percent, dropping from $0.60 to just $0.02.
- Kovri fork, creating more secure transactions with an I2P layer in C++ – I2P, known as the Invisible Internet Project, is a TOR alternative which would add a secure layer for all transactions pushed to the network. This was implemented after user anonimal pleaded with the Monero community who agreed to fund full-time development to make it a reality. (Gotta love crowdfunding)
- Monero Hardware wallet released – This project was organized and created as a funding mechanism in the Monero Forum Funding System (FFS) community. Michael Schloh von Bennewitz, software and maker veteran, as well as anonimal, lead developer of Kovri, spearheaded the project. Ledger and Trezor have also added XMR support.
- You can pay on Overstock with Monero – Thanks to Shapeshift and their API, Overstock now accepts Monero as well as several other altcoins. This shows further credibility to have the more mainstream adoption.
Roadmap
Monero has one of the most active development teams in crypto, so you shouldn’t be surprised that the project’s milestones are constantly evolving. Right now, the only two action items on their public roadmap for 2019 are:
- Second-layer scaling solutions
- Additional Monero Research Lab (MRL) research papers
Check the project’s roadmap regulularly to stay on top of what’s to come.
Trading
Having started in 2014, XMR didn’t see any relatively large price action until August 2016. At that time, the price went nearly vertical, jumping from around $1.80 (~0.003 BTC) to $13.17 (~0.0217 BTC). In less than a month, the USD price increased over 600 percent. That initial meteoric rise was most likely due to the increased popularity of XMR on the dark web as well as the coin’s first appearance on mainstream media.
Over its lifespan, the XMR price has ridden the typical rollercoaster of cryptocurrency prices. In the bull run of 2017 (RIP), the coin pulled a 10x to reach its all-time high of around $475.
As far as altcoins are concerned, XMR has done well. It tends to hold its value better than other coins during bear markets while still making significant strides during happier times.
With governments and corporations increasingly infringing on personal privacy, Monero should see steady demand from people who want to maintain their financial anonymity. Beyond dark web users, this base includes anyone who doesn’t want their spending habits or personal balances broadcast on a public ledger or under the eyeballs of a sometimes nefarious third-party. The persistent demand should give the XMR price a healthy floor.
You can purchase XMR on Binance with either BTC or ETH. If you’re looking to buy XMR directly with fiat, Bitfinex and Kraken are two additional options.
Although originally challenged by pool centralization, the recent fork away from ASIC miners caused the Monero (XMR) original pools hashrate to drop by more than 50%. The threat of secret ASIC mining prompted this fork. As a result, Monero still remains as a GPU mineable coin on What To Mine. Additionally, you can find a list of mining pools here.
How to Store XMR
There are a variety of desktop wallets for Monero with support on Linux, Mac, and Windows.
On the hardcore developer side, there are Arm (v7 & 8) OS for chipsets used in mobile devices as well as a source blockchain that allows you to procure a blockchain bootstrap from a raw file.
Mobile and light wallets include Cake Wallet, Monerujo, and My Monero.
If the extra security of a hardware wallet is more your jam, Ledger and Trezor both support XMR. Monero also has an internally-built wallet plan that was funded by the community and is currently in development.

Monero is indeed (and has been) happening.
Conclusion
Monero, a fork of Bytecoin, is a secure, private and untraceable currency. It utilizes the Cryptonote protocol alongside Ring Signatures, Ring Confidential Transaction and Stealth Addresses to protect user’s privacy.
The Monero community follows three key values: (1) Security, (2) Privacy and (3) Decentralization.
The core use cases behind Monero are transactions that are private, anonymous, and untraceable. It also has selective transparency which allows users to make certain transactions visible if desired. (E.g. an auditor or another party to prove the transaction) Ironically, this feature is attractive to many commercial interests that seek to protect critical business data and trade secrets.
On the scalability side, a block limit exists to facilitate more flexible data management (block sizes) and growth solutions. This was by design to allow flexibility in the growth of Monero’s architecture (which requires more cryptography and data around transactions) than most blockchains.
Although Monero has been a very steady and innovative player, this growth has not come without great struggles. The recent discovery of secret ASIC manufacturing of Monero miners has prompted the coin to be broken into 6 different forks.
This has not only divided the communities but raised concerns of what true decentralization means.
Despite these looming threats, the dedication of the team to building a robust and secure project continues. Privacy protocols like Kovri and hardware wallets like the Ledger Nano S continuously improving the ecosystem bodes well for the project. Additionally, the team continues to achieve development milestones.
Keep this secure, privacy coin on your radar. The team and community are leaders in the industry and will be one to watch indefinitely.
Editor’s Note: This article was updated by Steven Buchko on 1.9.19 to reflect the recent changes of the project.