You’ve probably heard of the Python module ‘dateutil‘. The module offers powerful extensions to the standard datetime library extensively used by Python developers. Yesterday, however, Sonatype’s automated malware detection system caught a suspicious PyPI package called ‘python-dateutils’ that mines Monero (XMR) cryptocurrency on your system—whether Windows, Linux, or macOS, and steals AWS credentials.
From the name of it, the package is a clear typosquatting attack impersonating one or more legitimate packages: dateutil, python-dateutil, or yet another legitimate PyPI package ‘dateutils‘. There is also some indication that in the past ‘python-dateutils’ could have been a legitimate library used by developers [1, 2].
But, versions of ‘python-dateutils’ caught by us this week are malicious. We’ve included the detailed analysis below.
Combines Base64 Obfuscation with ROT13 Cipher
Sonatype’s security research team has analyzed tens of thousands of malicious packages across npm, PyPI, and other open source ecosystems by now. And, over time we have come across several obfuscation techniques employed by threat actors—from steganography to base64-encoding, minification, and most recently, threat actors using a ready-made packer or obfuscator like JSDefender.
Unlike some of the novel techniques, ‘python-dateutils’ uses a straightforward base64-encoding for obfuscating text, some of which has been scrambled using the trivially reversible ROT13 cipher. Akin to the Caesar cipher of ancient times, ROT13 is a simple letter substitution cipher that replaces a letter with the 13th letter after it in the alphabet.
This becomes clear when we unpack one or more versions of the malicious ‘python-dateutils’ and peek into the setup.py manifest file:
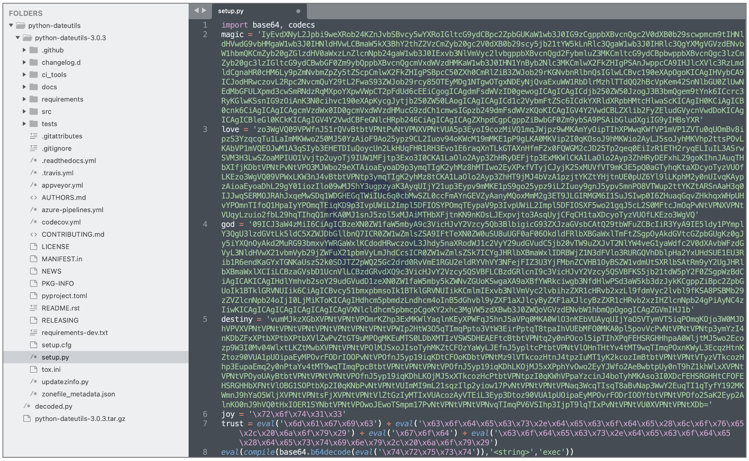
The strings toward the bottom of the file (lines 6-8) are mere hexadecimal representations of the aforementioned ASCII variable names (magic, love, god, etc.) and just another obscure method employed by the malware (Read more…)
