A financially-motivated threat actor notorious for its cryptojacking attacks has leveraged a revised version of their malware to target cloud infrastructures using vulnerabilities in web server technologies, according to new research.
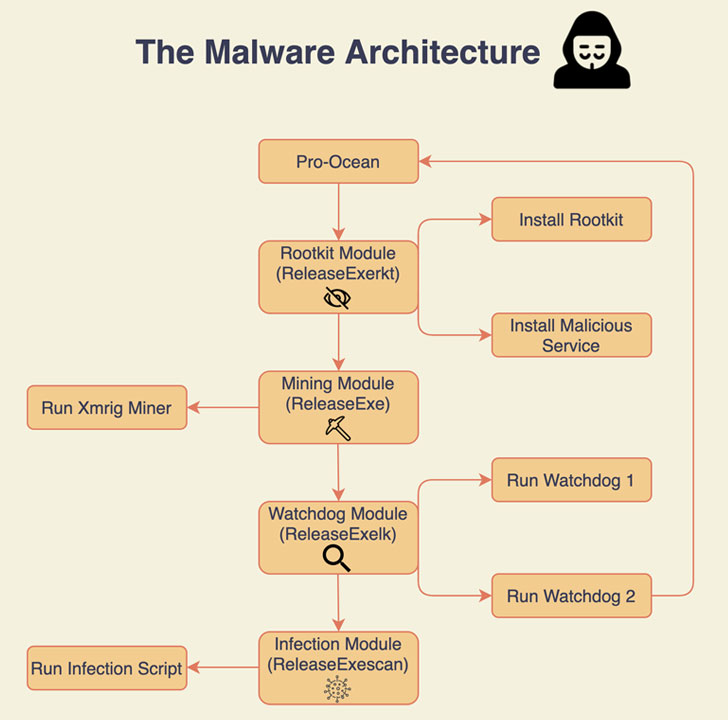
Deployed by the China-based cybercrime group Rocke, the Pro-Ocean cryptojacking malware now comes with improved rootkit and worm capabilities, as well as harbors new evasion tactics to sidestep cybersecurity companies’ detection methods, Palo Alto Networks’ Unit 42 researchers said in a Thursday write-up.
“Pro-Ocean uses known vulnerabilities to target cloud applications,” the researchers detailed. “In our analysis, we found Pro-Ocean targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances).”
“Once installed, the malware kills any process that uses the CPU heavily, so that it’s able to use 100% of the CPU and mine Monero efficiently.”
First documented by Cisco Talos in 2018, Rocke has been found to distribute and execute crypto-mining malware using a varied toolkit that includes Git repositories and different payloads such as shell scripts, JavaScript backdoors, as well as portable executable files.
While prior variants of the malware banked on the capability to target and remove cloud security products developed by Tencent Cloud and Alibaba Cloud by exploiting flaws in Apache Struts 2, Oracle WebLogic, and Adobe ColdFusion, Pro-Ocean has expanded the breadth of those attack vectors by aiming at Apache ActiveMQ, Oracle WebLogic, and Redis servers.
Besides its self-spreading features and better hiding techniques that allow it to stay under the radar and spread to unpatched software on the network, the malware, once installed sets about uninstalling monitoring agents to dodge detection and removing other malware and miners from the infected systems.
To achieve this, it takes advantage of a native Linux feature called LD_PRELOAD to mask its malicious activity, a library named Libprocesshider to stay hidden, and uses a Python infection script that takes the machine’s public IP to infect all machines in the same 16-bit subnetwork (e.g., 10.0.X.X).
Pro-Ocean also works to eliminate competition by killing other malware and miners, including Luoxk, BillGates, XMRig, and Hashfish, running on the compromised host. In addition, it comes with a watchdog module written in Bash that ensures persistence and takes care of terminating all processes that utilize more than 30% of the CPU with the goal of mining Monero efficiently.
“This malware is an example that demonstrates that cloud providers’ agent-based security solutions may not be enough to prevent evasive malware targeted at public cloud infrastructure,” Unit 42 researcher Aviv Sasson said. “This sample has the capability to delete some cloud providers’ agents and evade their detection.”