A nation-state actor known for its cyber espionage campaigns since 2012 is now using coin miner techniques to stay under the radar and establish persistence on victim systems, according to new research.
Attributing the shift to a threat actor tracked as Bismuth, Microsoft’s Microsoft 365 Defender Threat Intelligence Team said the group deployed Monero coin miners in attacks that targeted both the private sector and government institutions in France and Vietnam between July and August earlier this year.
“The coin miners also allowed Bismuth to hide its more nefarious activities behind threats that may be perceived to be less alarming because they’re ‘commodity’ malware,” the researchers said in an analysis published yesterday.
The primary victims of the attack have been traced to state-owned enterprises in Vietnam and entities with ties to a Vietnamese government agency.
The Windows maker likened Bismuth to OceanLotus (or APT32), linking it to spyware attacks using both custom and open-source toolsets to target large multinational corporations, governments, financial services, educational institutions, and human and civil rights organizations.
The development comes as OceanLotus was found leveraging a new macOS backdoor that enables the attackers to snoop on and steals confidential information and sensitive business documents from infected machines.
Using Coin Miners to Blend In
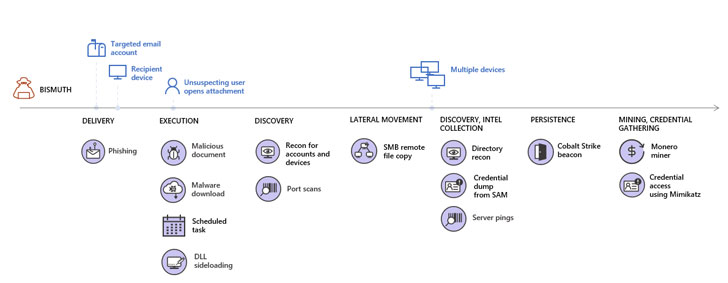
Although the group’s espionage and exfiltration tactics have essentially remained the same, the inclusion of coin miners in their arsenal points to a fresh way to monetize compromised networks, not to mention a crafty means of blending in and evading detection for as long as possible.
The idea is to buy time to move laterally and infect high-value targets like servers for further propagation.
To achieve this, tailored spear-phishing emails written in Vietnamese were crafted to specific recipients in a target organization, and in some cases, the threat actor even established correspondence with the targets in a bid to increase the chances of opening the malicious document embedded in the emails and trigger the infection chain.
A separate technique involved the use of DLL side-loading, wherein a legitimate library is replaced with a malicious variant, utilizing outdated versions of legitimate software such as Microsoft Defender Antivirus, Sysinternals DebugView, and Microsoft Word 2007 to load rogue DLL files and establish a persistent command-and-control (C2) channel to the compromised device and the network.
The newly established channel was then used to drop a number of next-stage payloads, including tools for network scanning, credential theft, Monero coin mining, and conducting reconnaissance, the results of which were transmitted back to the server in the form of a “.csv” file.
Hiding in Plain Sight
“Bismuth attacks put strong emphasis on hiding in plain sight by blending in with normal network activity or common threats that attackers anticipate will get low-priority attention,” Microsoft said.
“The combination of social engineering and use of legitimate applications to sideload malicious DLLs entail multiple layers of protection focused on stopping threats at the earliest possible stage and mitigating the progression of attacks if they manage to slip through.”
It’s recommended that businesses limit the attack surface used to gain initial access by beefing up email filtering and firewall settings, enforce credential hygiene, and turn on multi-factor authentication.