Cybercrime
,
Endpoint Security
,
Fraud Management & Cybercrime
Microsoft: Bismuth APT Tries to Distract Targets From Spying Tools
A hacking group recently deployed cryptocurrency miners within targeted victims’ networks to distract security teams from their cyberespionage campaigns, Microsoft reports.
The hacking group, which Microsoft calls Bismuth, used this cryptocurrency mining distraction technique to target government agencies and private organizations in France and Vietnam during July and August, Microsoft’s research determined.
See Also: Live Webinar | Securing Mobile Endpoints to Protect IP in the Pharma Industry
The use of the monero miners helped the hacking group establish persistence within targeted networks and enabled them to deploy other spy tools and malware without raising suspicion. That’s because cryptocurrency miners are usually low-level security priorities for most organizations, according to Microsoft.
“Cryptocurrency miners are typically associated with cybercriminal operations, not sophisticated nation-state actor activity,” the Microsoft report notes. “They are not the most sophisticated type of threats, which also means that they are not among the most critical security issues that defenders address with urgency. Recent campaigns from the nation-state actor Bismuth take advantage of the low-priority alerts coin miners cause to try and fly under the radar and establish persistence.”
The Microsoft report also notes: “While this actor’s operational goals remained the same – establish continuous monitoring and espionage, exfiltrating useful information as it surfaced – their deployment of coin miners in their recent campaigns provided another way for the attackers to monetize compromised networks.”
Starts With Phishing
The Bismuth attacks started with spear-phishing emails from a compromised Gmail account, Microsoft says.
“It’s likely the group conducted reconnaissance using publicly available sources and chose individual targets based on their job function,” the report notes. “Each email was sent to only one recipient at each target organization and used tailored subject lines and lure themes.”
Once the hackers gained an initial foothold in the network, they used a process known as Dynamic Link Library side-loading to gain additional persistence and to help them move laterally through the network, according to the report. This technique takes advantage of Windows applications and allows the attacker to load a malicious DLL to replace a legitimate one.
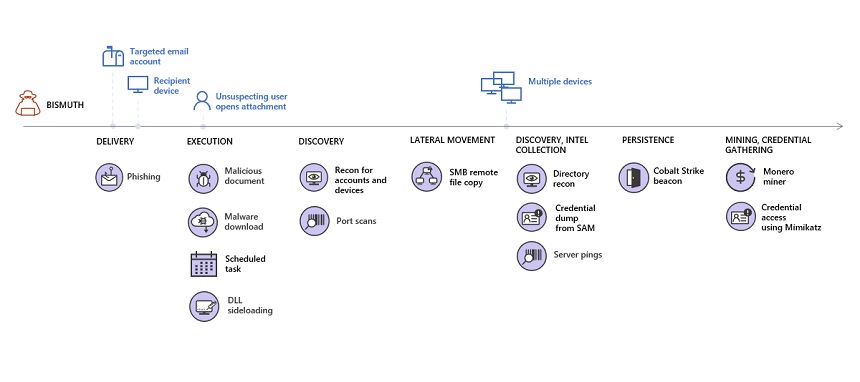
During the attack, the hackers planted applications, such as older versions of Windows 2007, in the targeted networks that were vulnerable to DDL side-loading. During this phase of the campaign, Microsoft researchers found custom malware called KerrDown that had been previously linked to the Bismuth group.
After spending about a month in the networks, the hacking group then deployed several PowerShell commands to collect credentials, connect to other devices using Windows Management Instrumentation and identity files and systems with data to exfiltrate later, according to the report. The hackers also deployed a weaponized version of Cobalt Strike.
Coin Miners
During the later stages of the attack, the Bismuth group deployed a series of monero miners that helped disguise the deployment of other malware within the networks. Once the cryptocurrency miners were deployed, the hackers used tools such as Mimikatz to steal data and additional credentials.
“As the affected organizations worked to evict Bismuth from their networks, Microsoft security researchers saw continued activity involving lateral movement to other devices, credential dumping and planting of multiple persistence methods,” according to the report. “This highlights the complexity of responding to a full-blown intrusion and the significance of taking quick action to resolve alerts that flag initial stages of an attack.”
Other Connections
The Microsoft report notes that Bismuth “shares similarities” with another hacking group known as OceanLotus or APT 32, which has been active since at least 2012 and is known for complex operations that target government agencies, multinational corporations, financial services, educational institutions and human and civil rights organizations. The group is believed to have ties to the government of Vietnam (see: Vietnamese APT Group Targets BMW, Hyundai: Report).
In November, security firm Trend Micro released a report that noted OceanLotus had developed an updated version of a backdoor it used to attack macOS devices (see: Fresh MacOS Backdoor Variant Linked to Vietnamese Hackers).
