- A botnet called Lemon Duck is spreading faster than ever, although it has been active since the end of December 2018.
- According to the research, it is one of the more complex mining botnets using Monero.
The botnet known as Lemon Duck has been infecting thousands of computers around the world since at least December 2018. It seems that recently the identification of the botnet has become far more difficult. It spreads through Windows 10 computers and is disguised as fake Covid-19 emails.
What’s going on with Lemon Duck?
Lemon Duck is not a simple botnet, it automatically spreads and delivers a variant of the Monero cryptocurrency mining software. The most recent report by Talos Intelligence shows the botnet has at least 12 independent infection vectors, meaning that it can spread across a network faster.
Botnet Infection Vectors
The majority of the spread originates in Asia, in countries like Iran, the Philippines, Vietnam, India, and Egypt. The main goal of the Lemon Duck botnet is to mine Monero using Windows, but also Linux in some cases. The code behind it is taken from open-source projects according to Talos Intelligence.
The Lemon Duck activity we recorded is consistent with a general uptick in cryptocurrency miners observed by Talos over the last several months, including a resurgence in PowerGhost, Prometei, and Tor2Mine.
The article also mentions a few ways users can try to detect and block this botnet and others. One of the main defenses vs any type of malware is the use of an Advanced Malware Protection software. Additionally, if users want to protect themselves further, web scanning software and email security software capable of blocking malicious emails will also help tremendously.
Monero bears look for a pullback
The Monero botnet has existed since December 2018, but can it actually have any impact on the price of the digital asset? According to a report released by Accenture Security, it can. Botnets mining Monero at scale can ‘generate massive quantities of the cryptocurrency worth millions of dollars’. The Smominru malware was able to mine around 24 XRM per day, close to $3,000 at current prices and around $10,000 at its peak.
XMR/USD daily chart
Although botnets do not have an immediate effect on the price of Monero, they can certainly add up to the selling pressure in the long term. On top of that, the TD sequential indicator has presented a sell signal on the daily chart that was not validated just yet because the price remained trading sideways.
The RSI is also quite overextended after a long uptrend that started on September 5. Monero hasn’t seen much of a pullback during the past month and a half. In the worst-case scenario, we could see XMR drop towards the 100-SMA at $100. Before that, there is also another price target of $115.
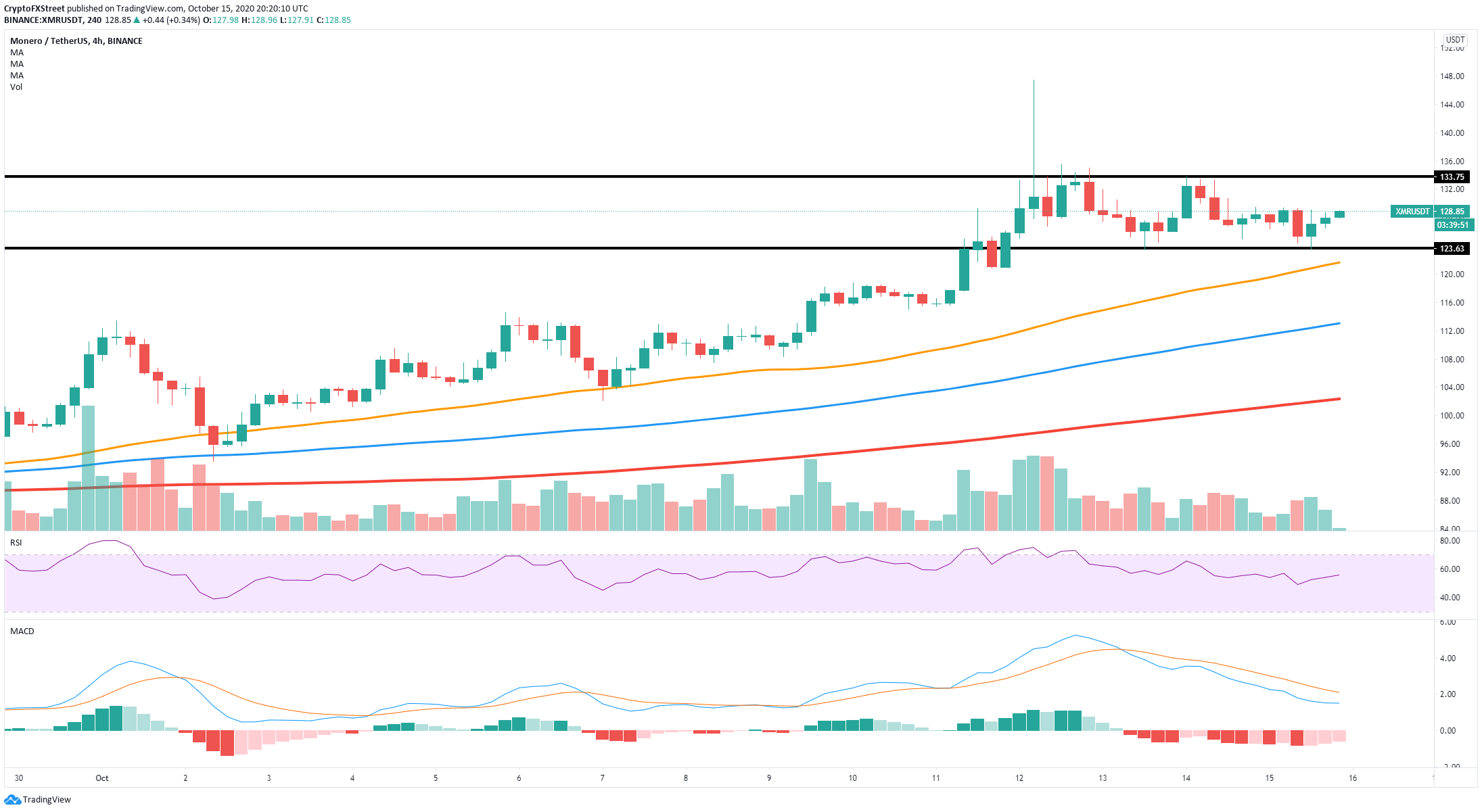
XMR/USD 4-hour chart
Nonetheless, on the 4-hour chart, the bulls managed to defend a critical support level at $123 and are eying up the resistance level at $133. The MACD is slowly shifting towards a bullish outlook and the RSI is not overextended here. A breakout above $133 could drive XMR up to $150.
Crucial price points to keep in mind
Monero could be close to topping out and bears are noticing. The nearest price target for XMR would be at $115, a support level established on October 10. Further down, there is also a critical level at $100 where the 100-SMA is located.
On the other hand, if the daily uptrend continues and bulls do not lose strength, we could see XMR climbing towards the resistance level at $133. A longer-term price target would be $150, the last high of the spike on October 12.