A computer popup box screen warning of a system being hacked, compromised software enviroment. 3D … [+]
getty
The Justice Department has announced action against two hacks of virtual currency exchanges by North Korean actors.
According to court documents, the actors stole millions of dollars’ worth of cryptocurrency and laundered the funds through Chinese over-the-counter (OTC) cryptocurrency traders. Now, the Justice Department is seeking to recover those funds through the filing of a civil forfeiture complaint.
(You can test your knowledge of civil forfeiture here.)
The complaint follows criminal and civil actions announced earlier this year related to the theft of cryptocurrency through other exchange hacks by North Korean actors. Those thefts initially occurred in 2018; afterward, the Internal Revenue Service-Criminal Investigation (IRS-CI) Cyber Crimes Unit learned that a South Korea-based virtual currency exchange had been hacked. The North Korean cyber actors responsible for the hack stole nearly $250 million worth of virtual currencies, which eventually landed in about 146 virtual currency accounts. In March of 2020, the United States filed a forfeiture complaint against those accounts.
The theft was not particularly surprising. Last year, a panel of experts established by the United Nations Security Council to investigate compliance with sanctions against North Korea found that the North Korean government has “used cyberspace to launch increasingly sophisticated attacks to steal funds from financial institutions and cryptocurrency exchanges to generate income.” Why? According to the panel, these activities allow North Korea “to generate income in ways that are harder to trace and subject to less government oversight and regulation than the traditional banking sector.” So far, these activities have raised money for the country’s weapons programs, with total proceeds to date estimated at up to $2 billion.
How does it happen? Money laundering through multiple accounts. Stolen funds can be transferred through accounts in a series of separate transactions and then routed to various countries before being converted to fiat currency. That makes it highly challenging to track the money. And if you change the kind of currency, it makes it even more difficult to trace. This practice of moving between different types of virtual currency is called “chain hopping.”
The most recent complaint detailed a theft that happened on or about July 1, 2019. In that hack, thieves stole approximately 401,981,748 Proton Tokens (PTT) from a virtual currency exchange. About 280,269,180 PTT was contained before it could be liquidated, but the remaining approximately 121,712,568 PTT entered the market. Around the same time, the affected exchange reported thefts of other currencies. Those currencies were transferred to other exchanges through a complicated series of transactions summarized in court documents like this:
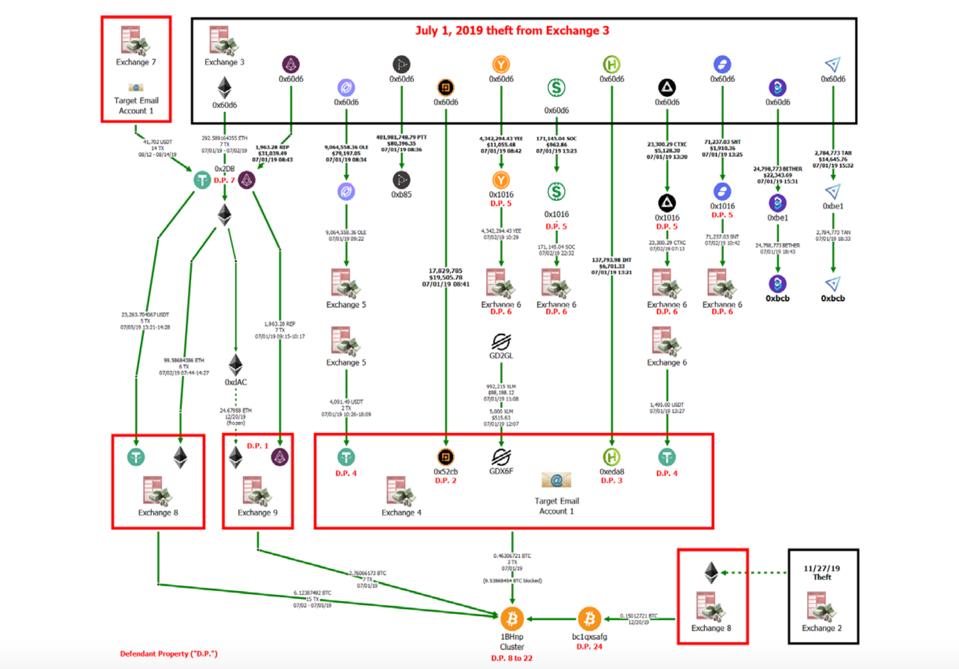
DOJ
According to the complaint, a few months later, in September 2019, a U.S.-based company focused on the Algorand blockchain (which administers ALGO tokens) was hacked in a related incident. The North Korea-associated hacker gained access to the company’s virtual currency wallets, funds held by the company on other platforms, and funds held by its partners. In the hack, the thieves used 15 recovery seeds to recreate wallets owned by the exchange and its partners. A recovery seed – also known as a recovery phrase – is a list of upwards of 12 words that, when entered in a specific order into virtual currency wallet software, allows whoever has the words to recreate access to virtual assets within the wallet. What the hackers were able to do then is direct the transfer of funds out of the wallets into other addresses and wallets. That allowed the hackers to steal nearly $2.5 million and launder it through 106 accounts at other virtual currency exchanges.
Following the transactions allowed law enforcement to identify the property involved in the schemes. The complaint now seeks a judgment declaring that the property be forfeited to the United States government.
“As part of our commitment to safeguarding national security, this office has been at the forefront of targeting North Korea’s criminal attacks on the financial system,” said Acting U.S. Attorney Michael R. Sherwin of the District of Columbia. “This complaint reveals the incredible skill of our Cryptocurrency Strike Force in tracing and seizing virtual currency, which criminals previously thought to be impossible.”
Several different agencies were involved in the investigation, including IRS-CI’s Washington, D.C. Cyber Crimes Unit, the FBI’s Chicago and Atlanta Field Offices, and HSI’s Colorado Springs Office with additional support from the FBI’s San Francisco Field Office.
Assistant U.S. Attorneys Zia M. Faruqui, Jessi Camille Brooks, and Christopher Brown, with assistance from Supervisory Paralegal Specialist Elizabeth Swienc and Legal Assistant Jessica McCormick, Trial Attorney C. Alden Pelker of the Criminal Division’s Computer Crime and Intellectual Property Section, and Trial Attorney David Recker of the National Security Division’s Counterintelligence and Export Control Section are prosecuting the case.
“Despite the highly sophisticated laundering techniques used, IRS-CI’s Cybercrimes Unit was able to successfully trace stolen funds directly back to North Korean actors,” said Don Fort, Chief of IRS Criminal Investigation (IRS-CI). “IRS-CI will continue to collaborate with its law enforcement partners to combat foreign and domestic operations that threaten the United States financial system and national security.”
The funds from these hacks, and the earlier hacks, were all allegedly laundered by the same group of Chinese OTC actors. The infrastructure and communication accounts used to further the intrusions and fund transfers were also tied to North Korea.
“At U.S. Cyber Command, we leverage a persistent engagement approach to challenge our adversaries’ actions in cyberspace,” said Brigadier General Joe Hartman, Commander of the Cyber National Mission Force. “This includes disrupting North Korean efforts to illicitly generate revenue. Department of Defense cyber operations do not occur in isolation. Persistent engagement includes acting through cyber-enabled operations as much as it does sharing information with our interagency partners to do the same.”
“Today’s complaint demonstrates that North Korean actors cannot hide their crimes within the anonymity of the internet. International cryptocurrency laundering schemes undermine the integrity of our financial systems at a global level, and we will use every tool in our arsenal to investigate and disrupt these crimes,” said Special Agent in Charge Emmerson Buie Jr. of the FBI’s Chicago Field Office. “The FBI will continue to impose risks and consequences on criminals who seek to undermine our national security interests.”
