- Cryptocurrency miners on Linux are wiping out each other as they’re looking to capture all system resources for themselves.
- Crooks are mining Monero and can make hundreds of USD in a few hours or days, depending on the system power.
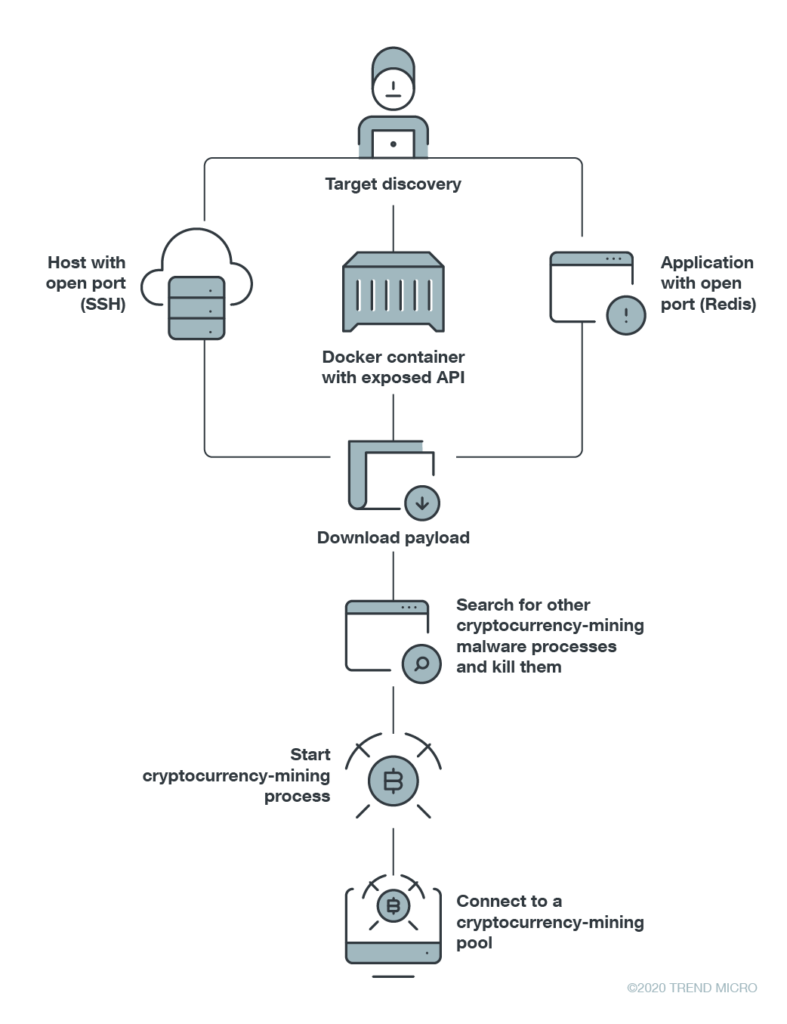
- Exploits include API misconfigurations, RCE vulnerabilities, and generally target unpatched systems.
Crooks are using the same or at least similar tools to scan systems and look for vulnerabilities, so when security holes are found, they are usually found by more than one hacker. Thus, we often see cases of malicious actors cleaning up previous infections and even taking steps to prevent future knocks.
When the exploit method involves cryptocurrency miners, this necessity becomes even more critical, as these malware tools need system resources to work effectively, and sharing these resources with other miners is not the ideal scenario.
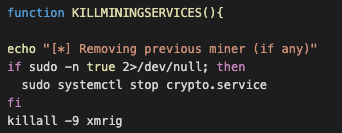
Trend Micro is diving deep into this matter, revealing how miners targeting Linux servers are fighting each other in a battle for resources. As the researchers report, widely used malware miners like “KORKERDS” and “Skidmap” scan for other miners in the host as soon as they establish their presence there. If any competing malware is found, the process is killed, and the tool is deleted from the system.
The scanning isn’t limited to resource-hungry processes, though, as hackers also search for Docker containers that could be mining crypto. This is something that has been going on since last year, so the crooks have already adapted to it.
Legitimate processes are also killed and removed, which is pretty audacious and risks early detection. This shows that hackers are going for short periods of complete system resource hogs, and that’s why they are targeting large and powerful server systems.
Finding a way in is usually a matter of finding an RCE (remote code execution) flaw to exploit. Trend Micro also reports on a recent trend of finding open APIs (application programming interfaces) that enable hackers to spawn new cryptomining containers or gain code execution privileges.
Trend Micro has taken a look at some of the Monero wallets linked with the malware samples they analyzed, and they ranged between a couple hundred to a thousand USD.
As for what system administrators can do against this threat, that would include applying available updates and security patches, using multifactor authentication where possible, utilizing access control policies, and only using verified and secure extensions.
API configurations on Docker and Redis should also be carefully reviewed and set to only allow requests that originate from the internal network and not from outside. If you absolutely need to allow SSH access, make sure that you use a powerful security solution that will keep an eye on what’s going on at all times.