A new cryptojacking botnet is spreading across compromised networks via multiple methods that include the EternalBlue exploit for Windows Server Message Block (SMB) communication protocol.
The attacker’s goal is to mine for Monero (XMR) cryptocurrency and enslave as many systems as possible for this task for increased profit.
Complex campaign
Researchers at Cisco Talos named the new botnet Prometei and determined that the actor has been active since March. They tagged the attacks as a complex campaign that relies on multi-modular malware.
To hop to computers on the network, the actor combines living-off-the-land binaries (LoLBins) like PsExec and WMI, SMB exploits, and stolen credentials.
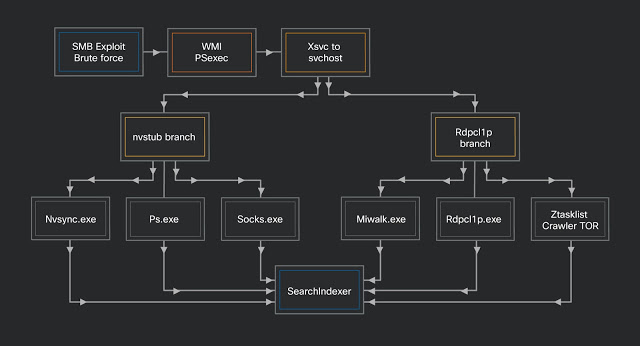
In all, the researchers counted more than 15 components in Prometei attacks, all managed by the main module, which encrypts (RC4) data before sending it to the command and control (C2) server via HTTP.
“Apart from a large focus on spreading across the environment, Prometei also tries to recover administrator passwords. The discovered passwords are sent to the C2 and then reused by other modules that attempt to verify the validity of the passwords on other systems using SMB and RDP protocols”
Tracking the botnet’s activity, the researchers noticed that its modules fall into two categories that have fairly distinct purposes: mining-related operations (dropping the miner, spreading on the network) and gaining access by brute-forcing logins using SMB and RDP.
Cisco Talos malware researcher Vanja Svajcer says that while the distinct functions and programming language (C++ and .NET) for these modules may indicate that another party is taking advantage of this botnet, it’s more likely that a single actor is controlling all of them.
Prometei is stealing passwords with a modified version of Mimikatz (miwalk.exe). These pass to the spreader module (rdpclip.exe) for parsing and authentication over an SMB session.
Should the credentials fail, the spreader launches a variant of the EternalBlue exploit for distributing and launching the main module (svchost.exe). Svajcer says that the author of the botnet is also aware of the SMBGhost vulnerability, although he did not find evidence of the exploit being used.
The last payload delivered on a compromised system is SearchIndexer.exe, which is version 5.5.3 of the XMRig open-source Monero mining software.
Evasion and anti-analysis
Prometei is unlike most mining botnets. Apart from organizing the tools by their purpose in the attack, it also features anti-detection and analysis evasion attributes.
Its author added layers of obfuscation from early versions of the bot, which grew more complex in later variants. The main module spreads on the network under various names (“xsvc.exe,” “zsvc.exe”) and uses a different packer that depends on an external file to be properly unpacked.
“In addition to making manual analysis more difficult, this anti-analysis technique also avoids detection in dynamic automated analysis systems” – Vanja Svajcer
Furthermore, Prometei can communicate with the C2 server using TOR or I2P proxies, too, to get instructions and send out stolen data.
The researcher says that the main module can also double as a remote access trojan, although the main functionality is Monero mining and possibly stealing Bitcoin wallets.
Prometei victims are located in the United States, Brazil, Pakistan, China, Mexico, and Chile. In four months, they earned the threat actor less than $5,000, or an average of $1,250 a month.
Based on the methods used to spread across the network and the modules employes, Svajcer believes that behind Prometei may be a professional developer likely from Eastern Europe.
