With Docker gaining popularity as a service to package and deploy software applications, malicious actors are taking advantage of the opportunity to target exposed API endpoints and craft malware-infested images to facilitate distributed denial-of-service (DDoS) attacks and mine cryptocurrencies.
According to a report published by Palo Alto Networks’ Unit 42 threat intelligence team, the purpose of these Docker images is to generate funds by deploying a cryptocurrency miner using Docker containers and leveraging the Docker Hub repository to distribute these images.
“Docker containers provide a convenient way for packaging software, which is evident by its increasing adoption rate,” Unit 42 researchers said. “This, combined with coin mining, makes it easy for a malicious actor to distribute their images to any machine that supports Docker and instantly starts using its compute resources towards cryptojacking.”
Docker is a well-known platform-as-a-service (PaaS) solution for Linux and Windows that allows developers to deploy, test, and package their applications in a contained virtual environment — in a way that isolates the service from the host system they run on.
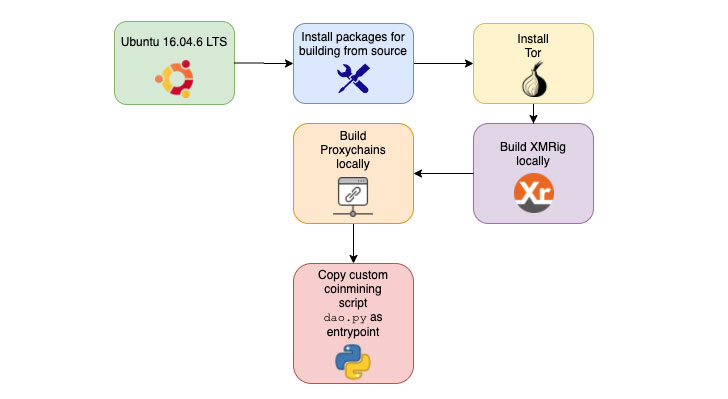
The now taken down Docker Hub account, named “azurenql,” consisted of eight repositories hosting six malicious images capable of mining Monero, a privacy-focused cryptocurrency.
The malware author behind the images used a Python script to trigger the cryptojacking operation and took advantage of network anonymizing tools such as ProxyChains and Tor to evade network detection.
The coin mining code within the image then exploited the processing power of the infected systems to mine the blocks.
The images hosted on this account have been collectively pulled over two million times since the start of the campaign in October 2019, with one of the wallet IDs used to earn more than 525.38 XMR ($36,000).
Exposed Docker Servers Targeted With DDoS Malware
That’s not all. In a new mass-scanning operation spotted by Trend Micro researchers, unprotected Docker servers are being targeted with at least two different kinds of malware — XOR DDoS and Kaiji — to collect system information and carry out DDoS attacks.
“Attackers usually used botnets to perform brute-force attacks after scanning for open Secure Shell (SSH) and Telnet ports,” the researchers said. “Now, they are also searching for Docker servers with exposed ports (2375).”
It’s worth noting that both XOR DDoS and Kaiji are Linux trojans known for their ability to conduct DDoS attacks, with the latter written entirely from scratch using Go programming language to target IoT devices via SSH brute-forcing.
The XOR DDoS malware strain works by searching for hosts with exposed Docker API ports, followed by sending a command to list all the containers hosted on the target server, and subsequently compromising them with the XORDDoS malware.
Likewise, the Kaiji malware scans the internet for hosts with exposed port 2375 to deploy a rogue ARM container (“linux_arm”) that executes the Kaiji binary.
“While the XOR DDoS attack infiltrated the Docker server to infect all the containers hosted on it, the Kaiji attack deploys its own container that will house its DDoS malware,” the researchers said, noting the difference between the two malware variants.
In addition, both the two pieces of malware gather details such as domain names, network speeds, process identifiers of running processes, and CPU and network information that are needed to mount a DDoS attack.
“Threat actors behind malware variants constantly upgrade their creations with new capabilities so that they can deploy their attacks against other entry points,” the researchers concluded.
“As they are relatively convenient to deploy in the cloud, Docker servers are becoming an increasingly popular option for companies. However, these also make them an attractive target for cybercriminals who are on the constant lookout for systems that they can exploit.”
It’s advised that users and organizations who run Docker instances immediately check if they expose API endpoints on the Internet, close the ports, and adhere to recommended best practices.